Free PCI Compliance Checklist
Prepared by: | [Your Name] |
Company Name: | [Your Company Name] |
Date: | May 1, 2050 |
Objective
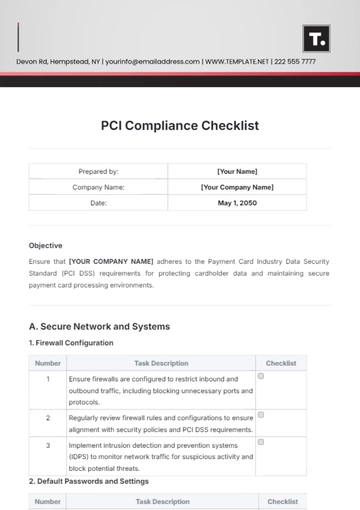
Ensure that [YOUR COMPANY NAME] adheres to the Payment Card Industry Data Security Standard (PCI DSS) requirements for protecting cardholder data and maintaining secure payment card processing environments.
A. Secure Network and Systems
1. Firewall Configuration
Number | Task Description | Checklist |
|---|---|---|
1 | Ensure firewalls are configured to restrict inbound and outbound traffic, including blocking unnecessary ports and protocols. | |
2 | Regularly review firewall rules and configurations to ensure alignment with security policies and PCI DSS requirements. | |
3 | Implement intrusion detection and prevention systems (IDPS) to monitor network traffic for suspicious activity and block potential threats. |
2. Default Passwords and Settings
Number | Task Description | Checklist |
|---|---|---|
1 | Change default passwords on all network devices, systems, and applications to strong, unique passwords. | |
2 | Disable or remove unnecessary services, ports, and accounts to reduce the attack surface. | |
3 | Enforce password complexity requirements and implement account lockout policies to protect against brute-force attacks. |
3. Network Segmentation
Number | Task Description | Checklist |
|---|---|---|
1 | Segment the network to separate the cardholder data environment (CDE) from non-sensitive areas. | |
2 | Implement VLANs, subnets, and access controls to restrict access to sensitive systems based on business needs. | |
3 | Monitor and log network traffic between segments to detect and prevent unauthorized access or data exfiltration. |
B. Cardholder Data Protection
1. Encryption
Number | Task Description | Checklist |
|---|---|---|
1 | Encrypt cardholder data using strong encryption algorithms and secure cryptographic protocols (e.g., AES, TLS). | |
2 | Protect encryption keys by storing them securely, separate from encrypted data, and ensuring access is limited to authorized personnel. | |
3 | Implement secure key management practices, including key rotation and periodic key changes, to enhance data protection. |
2. Secure Transmission
Number | Task Description | Checklist |
|---|---|---|
1 | Use secure communication channels (e.g., HTTPS, SFTP) to transmit cardholder data over public networks. | |
2 | Disable insecure protocols and services (e.g., FTP, Telnet) that transmit data in clear text. | |
3 | Implement strong access controls and authentication mechanisms to authenticate users and devices accessing cardholder data. |
3. Data Retention
Number | Task Description | Checklist |
|---|---|---|
1 | Limit the retention of cardholder data to only what is necessary for business operations and legal requirements. | |
2 | Develop and enforce data retention policies and procedures to securely delete or anonymize cardholder data when it is no longer needed. | |
3 | Implement data disposal methods, such as secure deletion and disk wiping, to ensure the permanent removal of cardholder data from storage devices. |
C. Vulnerability Management
1. Regular Scanning
Number | Task Description | Checklist |
|---|---|---|
1 | Conduct regular vulnerability scans of network systems, applications, and infrastructure using approved scanning vendors (ASVs) or internal tools. | |
2 | Schedule scans at least quarterly and after any significant changes to the network or system configurations. | |
3 | Remediate identified vulnerabilities promptly according to risk severity and potential impact on cardholder data security. |
2. Patch Management
Number | Task Description | Checklist |
|---|---|---|
1 | Establish a patch management process to identify, prioritize, and apply security patches and updates to systems and software. | |
2 | Implement automated patch management tools to streamline patch deployment and ensure timely patching of critical vulnerabilities. | |
3 | Test patches in a non-production environment before deploying them to production systems to minimize the risk of disruption or system instability. |
D. Access Control
1. User Authentication
Number | Task Description | Checklist |
|---|---|---|
1 | Implement multi-factor authentication (MFA) for all users accessing systems or applications that store, process, or transmit cardholder data. | |
2 | Enforce strong password policies, including minimum password length, complexity requirements, and password expiration periods. | |
3 | Monitor and review user access logs regularly to detect and investigate unauthorized access attempts or suspicious activity. |
E. Security Policies and Procedures
1. Information Security Policy
Number | Task Description | Checklist |
|---|---|---|
1 | Develop and maintain an information security policy that defines roles, responsibilities, and expectations for protecting cardholder data. | |
2 | Communicate the security policy to all employees and contractors, ensuring they understand their obligations to comply with PCI DSS requirements. | |
3 | Regularly review and update the security policy to reflect changes in technology, business operations, and regulatory requirements. |
2. Incident Response Plan
Number | Task Description | Checklist |
|---|---|---|
1 | Develop an incident response plan to detect, respond to, and recover from security incidents involving cardholder data breaches or unauthorized access. | |
2 | Test the incident response plan through tabletop exercises and simulations to evaluate effectiveness and identify areas for improvement. | |
3 | Establish procedures for notifying stakeholders, including payment card brands, regulators, and affected individuals, in the event of a data breach or security incident. |
F. Security Awareness Training
1. Employee Training
Number | Task Description | Checklist |
|---|---|---|
1 | Provide comprehensive security awareness training to all employees handling payment card data, covering phishing awareness, secure password practices, and data handling procedures. | |
2 | Conduct regular security awareness campaigns and refresher training sessions to reinforce security best practices and promote a culture of security awareness. | |
3 | Test employee knowledge and awareness through simulated phishing exercises and quizzes to assess the effectiveness of training programs. |
G. Compliance Reporting and Validation
1. Self-Assessment Questionnaire (SAQ)
Number | Task Description | Checklist |
|---|---|---|
1 | Complete and submit the appropriate Self-Assessment Questionnaire (SAQ) annually to validate compliance with PCI DSS requirements based on [YOUR COMPANY NAME]'s payment processing environment. | |
2 | Retain documentation and evidence of compliance for audit purposes, including completed SAQs, supporting documentation, and evidence of remediation activities. | |
3 | Engage qualified security assessors (QSAs) to conduct external audits and penetration tests to assess compliance with PCI DSS requirements and address any findings or deficiencies. |
Signature
By signing below, you acknowledge that you have reviewed and understand the contents of this PCI compliance checklist and affirm[YOUR COMPANY NAME]'s commitment to protecting cardholder data and complying with PCI DSS requirements.

[YOUR NAME]
Compliance Manager
Date: May 1, 2020
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Ensure seamless PCI compliance with Template.net's PCI Compliance Checklist Template. This editable and customizable tool streamlines your compliance process, tailored to your business needs. Easily modify and personalize it in our AI Editor Tool. Stay ahead of regulations effortlessly. Simplify compliance with Template.net.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist