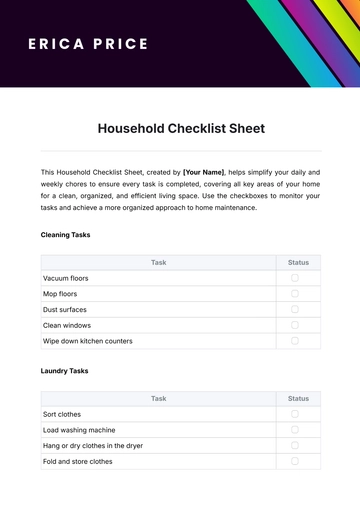
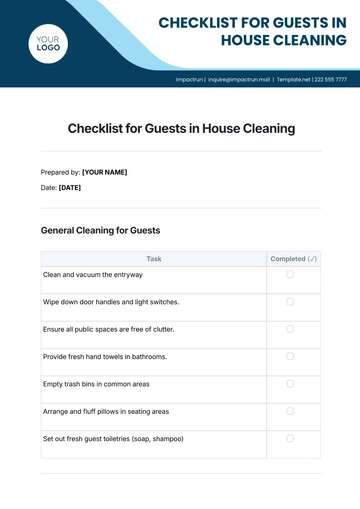
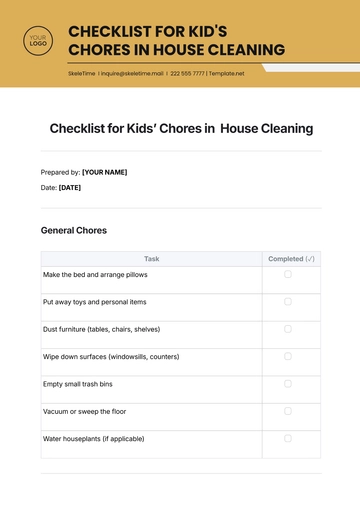
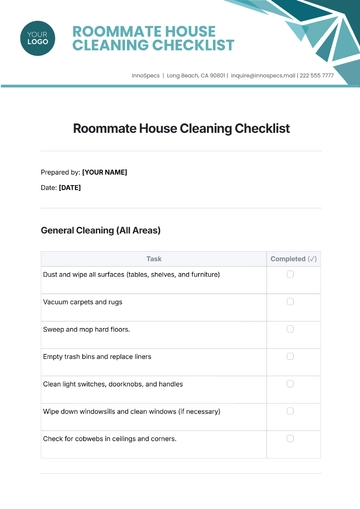
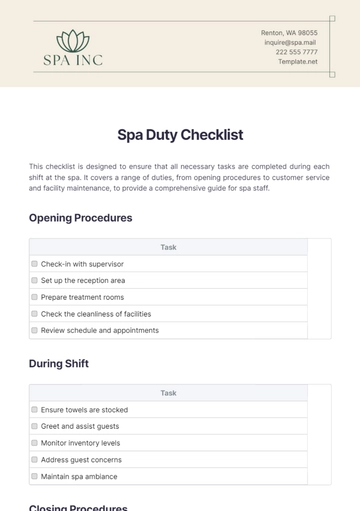
Free PII Compliance Checklist

I. Compliance Overview
Objective: Ensure that[YOUR COMPANY NAME] complies with regulations governing the protection of Personally Identifiable Information (PII).
Responsible Party: [YOUR NAME], PII Compliance Officer
Date of Last Review: [DATE]
Next Scheduled Review: [NEXT REVIEW DATE]
II. Regulatory Framework
1. Identify Applicable Regulations
Determine the specific regulations applicable to PII protection, such as GDPR, CCPA, HIPAA, or other industry-specific standards.
2. Familiarize with Requirements
Understand the requirements outlined in the applicable regulations regarding the collection, storage, and handling of PII.
III. Data Inventory
1. Identify PII Data
Conduct a thorough inventory of all PII collected, processed, or stored by the organization.
2. Categorize Data
Categorize PII data based on sensitivity and regulatory requirements for appropriate handling.
IV. Data Protection Measures
1. Data Encryption
Implement encryption protocols to protect PII data both in transit and at rest.
2. Access Controls
Establish access controls to limit access to PII data to authorized personnel only.
V. Data Privacy Policies
1. Privacy Policy Review
Review and update the organization's privacy policy to reflect current PII protection practices.
2. Transparency and Consent
Ensure transparency in data collection practices and obtain explicit consent from individuals for PII processing activities.
VI. Data Breach Response Plan
1. Develop Response Plan
Develop a comprehensive data breach response plan outlining procedures for detecting, reporting, and mitigating breaches involving PII.
2. Training and Awareness
Provide training to staff members on data breach response procedures and their roles in mitigating breaches.
VII. Vendor Management
1. Vendor Assessment
Assess the PII protection practices of third-party vendors and service providers with access to PII data.
2. Contractual Obligations
Establish contractual agreements with vendors outlining their responsibilities for protecting PII data.
VIII. Data Retention and Disposal
1. Retention Periods
Establish data retention periods based on regulatory requirements and business needs.
2. Secure Disposal
Implement procedures for securely disposing of PII data when it is no longer needed.
IX. Regular Audits and Assessments
1. Internal Audits
Conduct regular internal audits to assess compliance with PII protection measures and regulatory requirements.
2. External Assessments
Engage third-party assessors to conduct independent assessments of PII protection practices and identify areas for improvement.
X. Incident Reporting and Documentation
1. Incident Reporting Procedures
Establish procedures for reporting PII-related incidents, including unauthorized access or breaches.
2. Documentation
Maintain detailed records of PII-related incidents, including investigation findings and actions taken to remediate.
XI. Continuous Improvement
1. Review and Update
Regularly review and update PII protection practices and policies to adapt to changing regulations and emerging threats.
2. Staff Training
Provide ongoing training and awareness programs to staff members to ensure compliance with PII protection measures.
XII. Signature
By signing below, you acknowledge that you have reviewed and understand the contents of this PII compliance checklist.

PII Compliance Officer
Date: [DATE]
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Discover peace of mind with our PII Compliance Checklist Template from Template.net. This editable and customizable resource ensures your data protection strategies are on point. Seamlessly modify it using our AI Editor Tool, empowering your compliance journey effortlessly. Stay secure and efficient with this essential template
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist