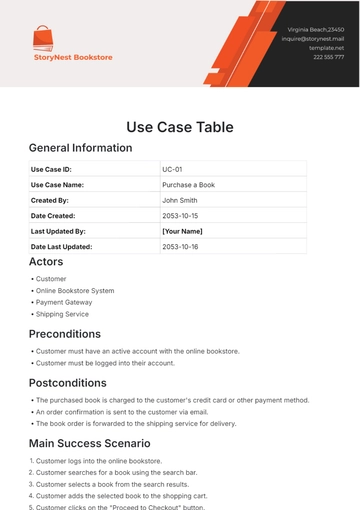
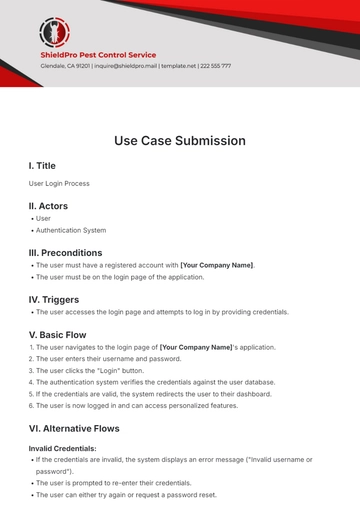
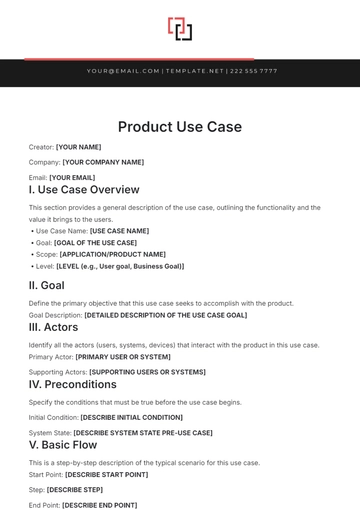
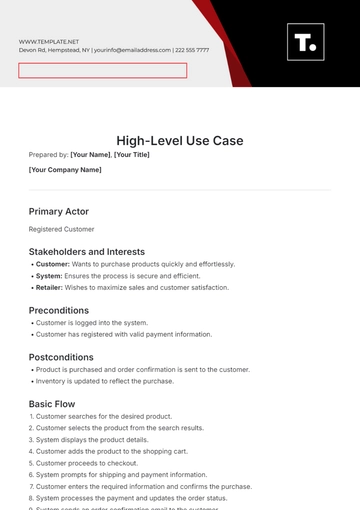
Free Basic Use Case Outline

I. Use Case Identification
Use Case ID: UCT-001
Title: Manage [Your Functionality]
Created By: [Your Name]
Date Created: [Date]
Last Updated: [Date]
Version: 1.0
II. Use Case Description
This section provides a general description of what the use case is intended to accomplish.
Goal: To enable [Your Role] to [Your Goal] effectively and efficiently.
Scope: [Your System Name]
Level: User-goal level
Preconditions:
[Your System Name] is operational.
The user is authenticated and authorized to perform actions related to this use case.
Postconditions:
The system updates and reflects changes made by [Your Role].
Notifications are sent out if necessary.
III. Actors
Primary Actor: [Your Role]
Secondary Actors: [Other Relevant Roles]
IV. Stakeholders and Interests
[Your Role]: Wants to ensure that [Needs or Goals] are met through the use of the system.
[Other Relevant Roles]: Interested in [Their Interests] which are impacted by the outcome of this use case.
V. Use Case Triggers
Triggering Event: This use case starts when [Event or Action Initiating the Use Case].
VI. Main Success Scenario (Basic Flow)
[Your Role] starts the action by [Specific Action].
The system validates that [Your Role] has the necessary permissions.
The system processes the request and updates the database.
The system displays a confirmation message to [Your Role].
The system sends out notifications to [Other Relevant Roles] if necessary.
VII. Extensions (Alternative Flows)
If the user does not have permission:
The system displays an error message.
The use case ends.
If the system cannot process the request:
The system logs the error.
The system notifies [Your Role] of the issue.
[Your Role] may attempt the request again or contact support.
VIII. Special Requirements
Performance Requirements: Actions must be processed within [X Seconds/Minutes].
Security Requirements: All data must be transmitted securely using [Encryption/Protocol].
IX. Assumptions
[Your System Name] is regularly maintained and updated.
Users are familiar with the basic operations of [Your System Name].
X. Frequency of Use
This use case is expected to be used [X] times a [Day/Week/Month] by [Your Role].
XI. Miscellaneous
Diagrams: Include any UML or process diagrams if applicable.
Notes: Any additional notes or comments related to this use case.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Document essential system interactions with the Basic Use Case Template from Template.net. This editable and customizable template offers a simple structure for capturing core user scenarios and system processes. Use our AI Editor Tool to create a clear and organized outline that ensures comprehensive understanding and documentation of use cases for your project.