Free Cloud Security Assessment Checklist
Prepared by: [YOUR NAME]
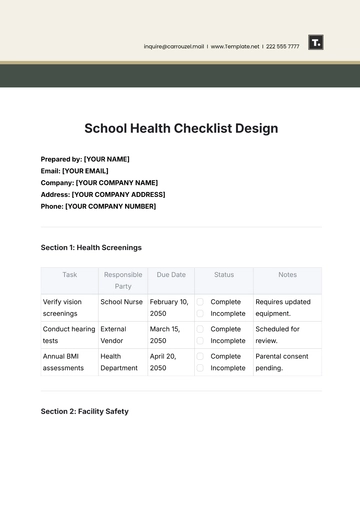
Cloud Service Provider Assessment:
Scrutinize the cloud service provider's security policies to ensure they align with industry best practices, covering data confidentiality, integrity, and availability. | |
Evaluate the efficacy of the provider's data encryption methods, focusing on both data in transit and at rest, to mitigate the risk of unauthorized access. | |
Assess the robustness of the disaster recovery plan, verifying its ability to swiftly restore operations in the event of disruptions or data loss. | |
Review the provider's procedures for handling information, emphasizing secure data processing, storage, and transmission practices. | |
Ensure the cloud provider adheres to industry security standards, reinforcing your commitment to regulatory requirements. |
User Access and Identity Management:
Verify the implementation of strong password policies, promoting the use of complex passwords to fortify user account protection. | |
Assess the implementation of two-factor authentication as an additional layer of security to thwart unauthorized access attempts. | |
Review and define user access levels and permissions, limiting privileges to the minimum necessary for operational tasks. | |
Scrutinize user activity logs for any signs of suspicious behavior, enabling swift detection and response to potential security incidents. | |
Ensure frequent audits of user access roles are conducted, guaranteeing the ongoing relevance and necessity of assigned permissions. |
Data Protection and Privacy:
Verify compliance with data protection regulations such as GDPR and CCPA, ensuring data processing aligns with legal requirements. | |
Examine data encryption and decryption processes to safeguard data confidentiality and maintain the integrity of sensitive information. | |
Assess the effectiveness of data loss prevention strategies to mitigate the risk of unauthorized data exposure. | |
Check for regular backups and reliable restore procedures to facilitate swift recovery in the event of data loss or corruption. | |
Review procedures in place to handle data breaches, emphasizing a swift and effective response to minimize potential damage. |
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Secure your digital environment through this ultimate Cloud Security Assessment Checklist Template. This editable and customizable solution, exclusively found in Template.net, ensures comprehensive coverage of your cloud security needs. Seamlessly adapt and refine your security protocols directly in our Ai Editor Tool, ensuring a robust defense for your cloud infrastructure.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist