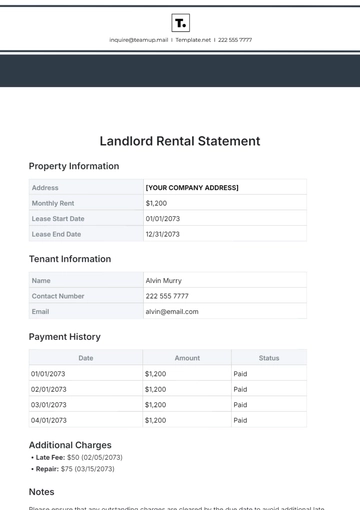
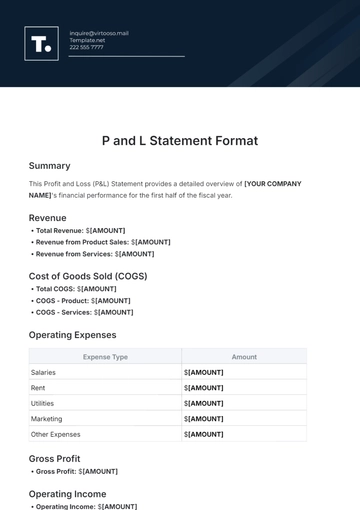
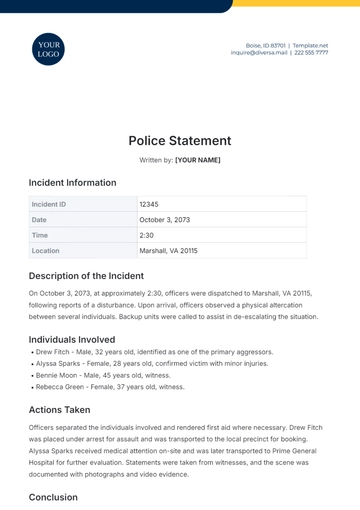
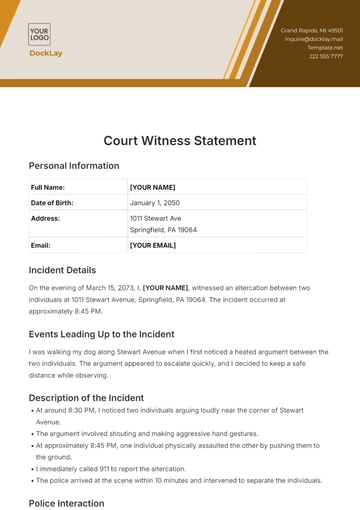
Free Financial Decision Statement

This Financial Decision Statement provides a clear and structured roadmap for [Your Company Name] to enhance its cybersecurity infrastructure, a critical step in safeguarding our digital assets and reinforcing client confidence in our data handling capabilities.
1. Decision Overview
a. Purpose of Decision: The primary objective of this decision is to invest in upgrading [Your Company Name]'s cybersecurity infrastructure. This includes the adoption of advanced security software and hardware enhancements.
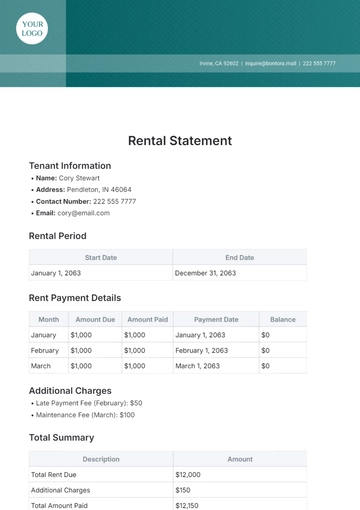
b. Scope and Impact: The decision encompasses a company-wide upgrade, impacting all departments. The expected outcome is enhanced data security, reduced risk of data breaches, and improved client trust, which is crucial for maintaining [Your Company Name]'s market reputation.
2. Background and Rationale
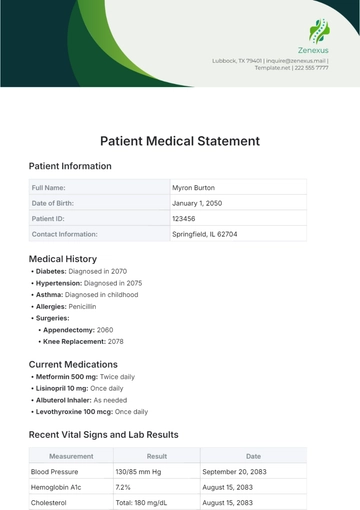
a. Market and Internal Analysis: In light of recent increases in cyber threats and a comprehensive analysis of our IT infrastructure's vulnerabilities, this upgrade is imperative. Our current systems are outdated and susceptible to new types of cyber-attacks.
b. Justification: The investment aligns with our strategic goal of maintaining the highest standards of data security. It ensures compliance with emerging data protection regulations and addresses client concerns about data safety.
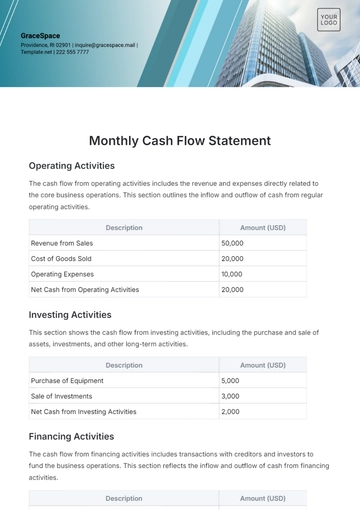
3. Financial Implications
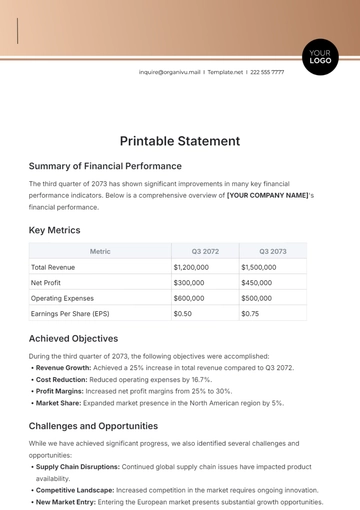
a. Cost-Benefit Analysis: The projected cost of the upgrade is [$1 million]. The benefits include avoiding potential losses from data breaches, estimated at [$5 million] annually, and retaining client trust.
b. ROI Estimation: We anticipate a return on investment of [50%] within [two years], factoring in cost savings from enhanced security and the potential for attracting more clients due to improved trust.
4. Risks and Mitigation Strategies
a. Risk Assessment: Key risks include potential operational disruptions during the upgrade and the challenge of staff adapting to new systems.
b. Mitigation Measures: To minimize these risks, the upgrade will be implemented in phases outside of peak business hours. Comprehensive staff training will be provided to ensure a smooth transition.
5. Implementation and Monitoring
a. Implementation Plan: The upgrade will be executed over six months, starting with critical business areas. An external cybersecurity firm will be engaged to assist with the implementation.
b. Monitoring and Review Mechanisms: The IT department will monitor system performance and security metrics post-implementation. Regular reviews will be conducted to assess effectiveness and make necessary adjustments.
Prepared by:
[Your Name]
[Job Title]
[Date]
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Introducing Template.net's Financial Decision Statement Template. It's fully editable and customizable, thanks to our AI Editor Tool. Make informed financial decisions with ease using this comprehensive template. Empower yourself to analyze, plan, and strategize effectively for your financial future with Template.net's innovative solutions.