Free Sample Use Case
I. Use Case Identification
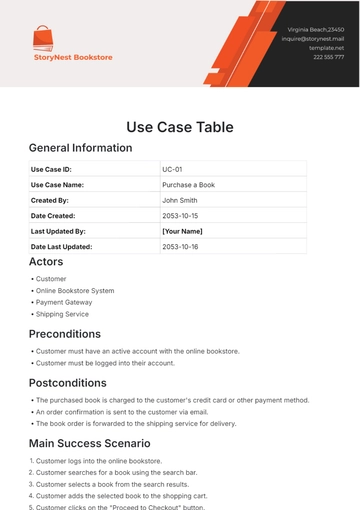
Use Case ID: UC-001
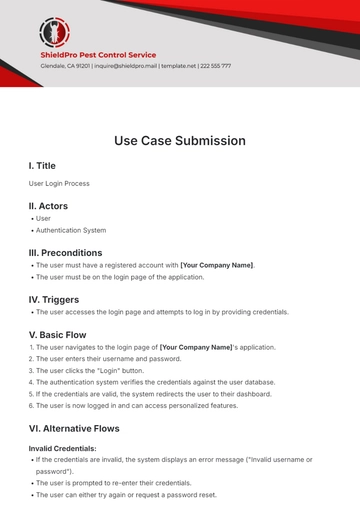
Title: User Authentication
Created By: [YOUR NAME]
Date Created: [DATE]
Last Updated: [DATE]
Version: 1.0
II. Objective
This use case aims to outline the process by which a user authenticates themselves within the system.
III. Scope
In-Scope: User authentication process
Out-of-Scope: User registration, password recovery
IV. Stakeholders
Stakeholder | Role | Responsibility |
|---|---|---|
User | End User | Needs to securely log in to access the system |
System Administrator | Admin | Manages user accounts and access permissions |
V. Actors
Primary Actor: User
Secondary Actor: System
VI. Preconditions
The user has a registered account in the system.
The user is on the login page.
VII. Trigger
The user enters their username and password and clicks the "Login" button.
VIII. Main Flow
The system displays the login page.
The user enters their username and password.
The system verifies the credentials.
If the credentials are valid, the system grants access to the user.
If the credentials are invalid, the system displays an error message.
IX. Alternate Flows
Invalid Credentials:
The system prompts the user to re-enter their credentials.
After three unsuccessful attempts, the system locks the user's account.
X. Postconditions
If the credentials are valid, the user gains access to the system.
If the credentials are invalid, the user receives an error message and is prompted to retry.
XI. Special Requirements
All user credentials must be securely stored and encrypted.
The system should include CAPTCHA or other security measures to prevent automated login attempts.
XII. Assumptions
Users have previously registered accounts with valid credentials.
The system infrastructure supports secure authentication protocols.
XIII. Frequency of Use
This use case is expected to be utilized multiple times daily by all registered users.
XIV. Miscellaneous
Diagrams: Include any relevant diagrams illustrating the authentication process.
Notes: Any additional notes or considerations relevant to the use case.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Introducing the Sample Use Case Template from Template.net, your solution for crafting compelling scenarios effortlessly. This editable and customizable template empowers you to tailor your use cases to perfection, ensuring precision in communication. Seamlessly editable in our AI Editor Tool, streamline your workflow and elevate your presentations with ease.