Free Use Case

I. Use Case Identification
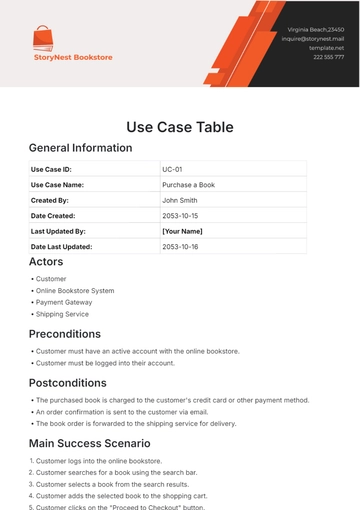
Use Case ID: UCT-001
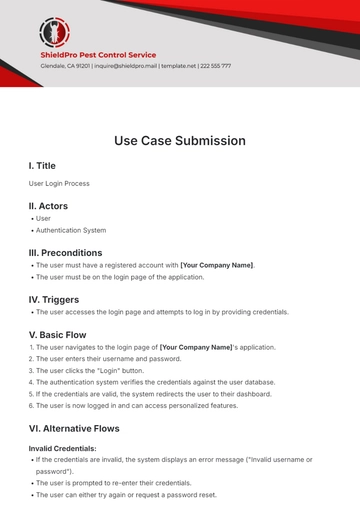
Title: Manage [YOUR FUNCTIONALITY]
Created By: [YOUR NAME]
Date Created: [DATE]
Last Updated: [DATE]
Version: 1.0
II. Use Case Description
This section provides a general description of what the use case is intended to accomplish.
Goal: To enable [YOUR ROLE] to [YOUR GOAL] effectively and efficiently.
Scope: [YOUR SYSTEM NAME]
Level: User-goal level
Preconditions:
[YOUR SYSTEM NAME] is operational.
The user is authenticated and authorized to perform actions related to this use case.
Postconditions:
The system updates and reflects changes made by [YOUR ROLE].
Notifications are sent out if necessary.
III. Actors
Primary Actor: [YOUR ROLE]
Secondary Actors: [OTHER RELEVANT ROLES]
IV. Stakeholders and Interests
[YOUR ROLE]: Wants to ensure that [NEEDS OR GOALS] are met through the use of the system.
[OTHER RELEVANT ROLES]: Interested in [THEIR INTERESTS] which are impacted by the outcome of this use case.
V. Use Case Triggers
Triggering Event: This use case starts when [EVENT OR ACTION INITIATING THE USE CASE].
VI. Main Success Scenario (Basic Flow)
[YOUR ROLE] starts the action by [SPECIFIC ACTION].
The system validates that [YOUR ROLE] has the necessary permissions.
The system processes the request and updates the database.
The system displays a confirmation message to [YOUR ROLE].
The system sends out notifications to [OTHER RELEVANT ROLES] if necessary.
VII. Extensions (Alternative Flows)
2a. If the user does not have permission:
The system displays an error message.
The use case ends.
3a. If the system cannot process the request:
The system logs the error.
The system notifies [YOUR ROLE] of the issue.
[YOUR ROLE] may attempt the request again or contact support.
VIII. Special Requirements
Performance Requirements: Actions must be processed within [X SECONDS/MINUTES].
Security Requirements: All data must be transmitted securely using [ENCRYPTION/PROTOCOL].
IX. Assumptions
[YOUR SYSTEM NAME] is regularly maintained and updated.
Users are familiar with the basic operations of [YOUR SYSTEM NAME].
X. Frequency of Use
This use case is expected to be used [X] times a [DAY/WEEK/MONTH] by [YOUR ROLE].
XI. Miscellaneous
Diagrams: Include any UML or process diagrams if applicable.
Notes: Any additional notes or comments related to this use case.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Discover the perfect Use Case Template on Template.net! Our editable and customizable design lets you tailor your project effortlessly. Plus, it's fully editable in our AI Editor Tool, ensuring seamless adjustments for your unique needs. Elevate your presentations with precision and style!