Free Cyber Security Audit Checklist
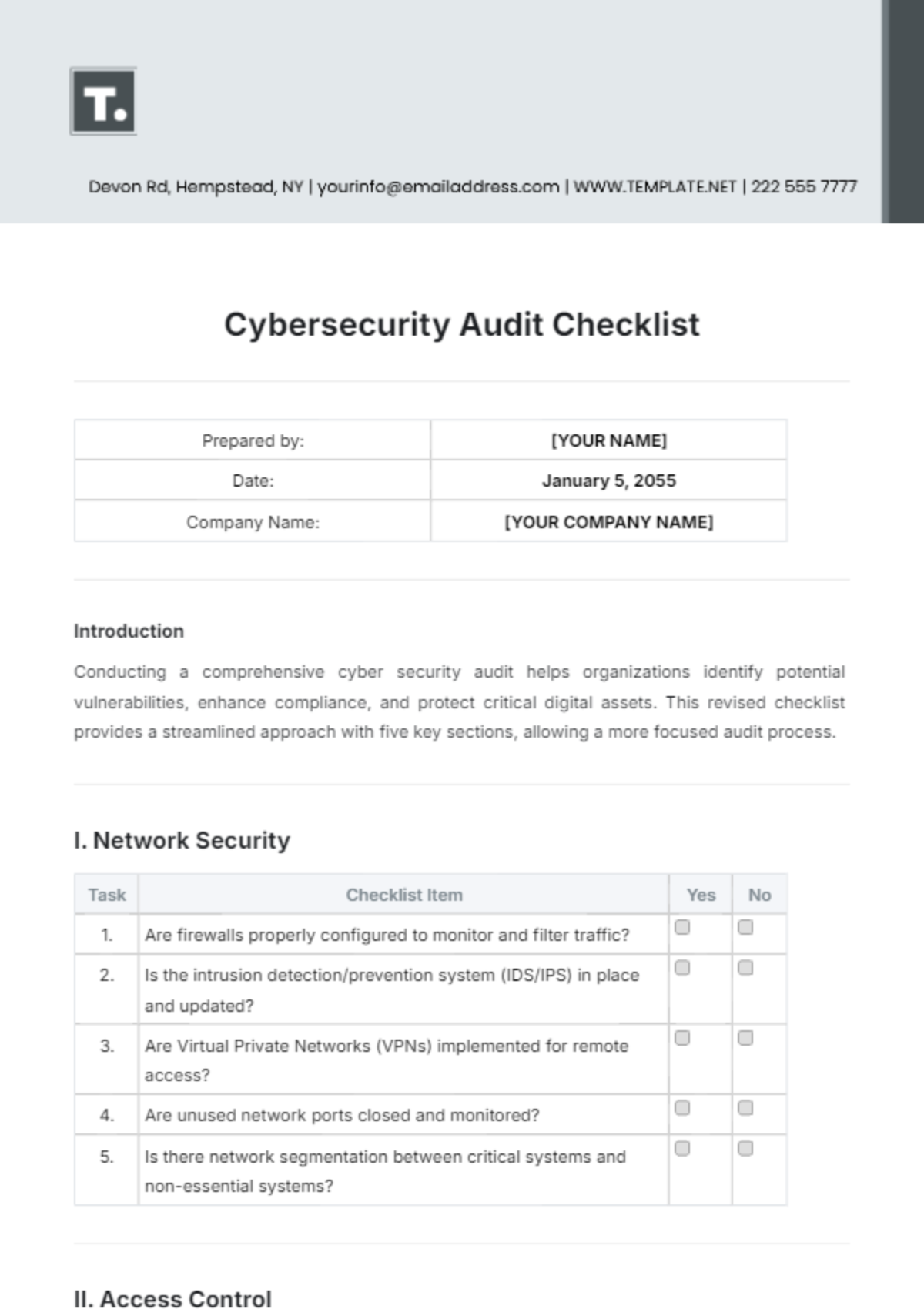
Prepared by: | [YOUR NAME] |
Date: | January 5, 2055 |
Company Name: | [YOUR COMPANY NAME] |
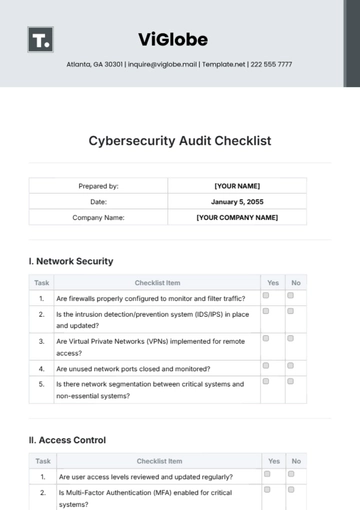
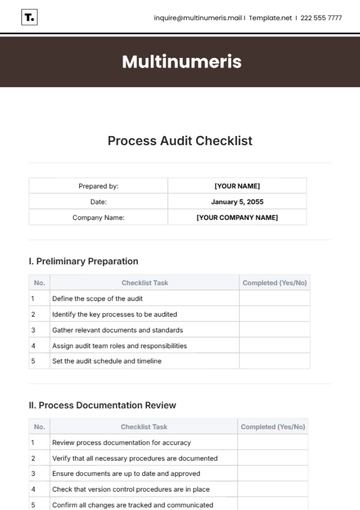
I. Network Security
Task | Checklist Item | Yes | No |
|---|---|---|---|
1. | Are firewalls properly configured to monitor and filter traffic? | ||
2. | Is the intrusion detection/prevention system (IDS/IPS) in place and updated? | ||
3. | Are Virtual Private Networks (VPNs) implemented for remote access? | ||
4. | Are unused network ports closed and monitored? | ||
5. | Is there network segmentation between critical systems and non-essential systems? |
II. Access Control
Task | Checklist Item | Yes | No |
|---|---|---|---|
1. | Are user access levels reviewed and updated regularly? | ||
2. | Is Multi-Factor Authentication (MFA) enabled for critical systems? | ||
3. | Are processes in place to manage access for new hires and terminated employees? | ||
4. | Are privileged accounts restricted and monitored for suspicious activity? | ||
5. | Is there a password policy enforcing complexity and expiration rules? |
III. Data Protection
Task | Checklist Item | Yes | No |
|---|---|---|---|
1. | Is sensitive data encrypted in transit and at rest? | ||
2. | Are regular data backups performed and stored securely off-site? | ||
3. | Are Data Loss Prevention (DLP) tools in place to prevent unauthorized data sharing? | ||
4. | Is third-party data access properly managed and secured? | ||
5. | Is there a response plan for data breaches, including notification procedures? |
IV. Application Security
Task | Checklist Item | Yes | No |
|---|---|---|---|
1. | Are applications regularly tested for vulnerabilities (e.g., using penetration testing)? | ||
2. | Are outdated software applications removed from the system? | ||
3. | Are patches and updates applied regularly to all software and systems? | ||
4. | Are Web Application Firewalls (WAF) in place for web applications? | ||
5. | Is there a secure coding policy guiding developers? |
V. Incident Response and Recovery
Task | Checklist Item | Yes | No |
|---|---|---|---|
1. | Is there a documented and regularly updated incident response plan? | ||
2. | Are incident response drills or tabletop exercises conducted regularly? | ||
3. | Are staff trained on their roles in incident response processes? | ||
4. | Are forensic tools available to investigate and contain incidents? | ||
5. | Is there a plan for post-incident recovery and system restoration? |
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Presenting the professionally designed Cyber Security Audit Checklist Template, available exclusively on Template.net. Enhance your security protocols with this editable and customizable checklist, carefully designed for smooth risk assessment. Ensure strong protection by adapting it to your specific requirements using our intuitive Ai Editor Tool, effortlessly securing your digital assets.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist