Free IT Management Requirements

1. Introduction
The IT Management Requirements document specifies the necessary criteria and specifications for the management and administration of IT systems within [Your Company Name]. This document aims to align IT initiatives with business objectives, enhance operational efficiency, and ensure compliance with industry standards.
2. Objectives
The primary objectives of these IT Management Requirements are:
Ensure Alignment with Business Goals: Align IT systems and processes with the organization’s strategic objectives.
Enhance Operational Efficiency: Improve the efficiency of IT operations by streamlining processes and reducing downtime.
Guarantee Compliance: Ensure adherence to regulatory standards such as GDPR and industry best practices.
Optimize Resource Utilization: Maximize the use of IT resources, including hardware and software, to minimize costs and improve performance.
3. Stakeholders
Stakeholder Group | Role and Responsibility |
|---|---|
IT Managers | Oversee the implementation and management of IT systems. |
System Administrators | Maintain and support IT infrastructure and services. |
Developers | Design and develop IT solutions based on requirements. |
End Users | Utilize IT systems and provide feedback on their effectiveness. |
Senior Management | Provide strategic direction and approve major IT initiatives. |
4. Functional Requirements
4.1 System Capabilities
User Management: The system must allow administrators to create, modify, and delete user accounts efficiently, supporting role-based access control.
Data Management: Capabilities must include secure storage, retrieval, and backup of organizational data, with redundancy to prevent data loss.
Reporting: The system should include tools to generate performance and usage reports, including real-time dashboards and historical data analysis.
Integration: The IT solution must integrate seamlessly with existing enterprise systems, including CRM, ERP, and email platforms.
4.2 Performance
Response Time: The system must respond to user queries within 2 seconds to ensure a smooth user experience.
Availability: Systems should maintain 99.9% uptime, with scheduled maintenance windows communicated in advance.
Scalability: The solution should handle a 25% increase in user load without significant performance degradation, allowing for future growth.
5. Non-Functional Requirements
5.1 Security
Access Control: Implement role-based access controls to restrict unauthorized access to sensitive data and systems.
Data Encryption: All sensitive data must be encrypted both in transit and at rest to protect against unauthorized access and breaches.
Audit Trails: Maintain detailed logs of all system access and modifications to support auditing and compliance efforts.
5.2 Usability
User Interface: The system must feature an intuitive and user-friendly interface designed to minimize training requirements and enhance productivity.
Training: Provide comprehensive training materials and sessions for end users, including user guides and hands-on workshops.
5.3 Compliance
Regulatory Compliance: Ensure the IT systems adhere to GDPR, HIPAA, and other relevant regulations to avoid legal and financial penalties.
Industry Standard: Follow best practices as outlined by ITIL and ISO/IEC standards to ensure high-quality service delivery and continuous improvement.
6. Constraints
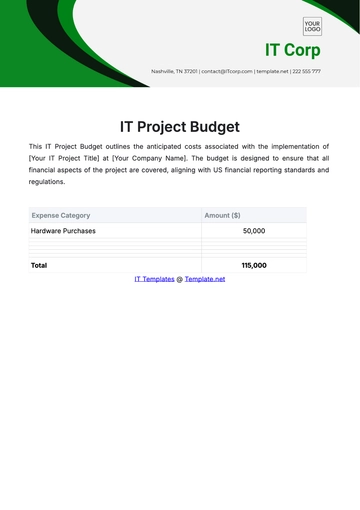
Budgetary Limitations: All IT projects must adhere to the allocated budget of $500,000 per year, including hardware, software, and personnel costs.
Technical Limitations: The solution must be compatible with existing hardware, including servers and networking equipment, and integrated with current software applications.
Time Constraints: Projects must be completed within a 6-month timeline, with milestones and deliverables defined in the project plan.
7. Assumptions
Stable Infrastructure: Assumes that the existing IT infrastructure, including network and hardware, will remain stable throughout the project.
User Cooperation: Assumes that end users will participate in required training sessions and provide timely feedback for system improvements.
Vendor Reliability: Assumes that third-party vendors will deliver products and services as specified in their contracts and within agreed-upon timelines.
8. Acceptance Criteria
Criteria | Description |
|---|---|
Functional Validation | It is necessary to fully meet all functional requirements. |
Performance Benchmarks | Systems must meet or exceed specified performance metrics. |
Security Audits | Successful completion of security audits without major findings. |
User Acceptance Testing | Positive feedback from end users during the testing phases. |
9. Glossary
GDPR: General Data Protection Regulation.
HIPAA: Health Insurance Portability and Accountability Act.
ITIL: Information Technology Infrastructure Library.
ISO/IEC: International Organization for Standardization / International Electrotechnical Commission.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Introducing the IT Management Requirements Template from Template.net—your go-to solution for streamlined project planning. This fully editable template is customizable to fit your specific needs and can be easily modified using our AI Editor Tool. Enhance your IT projects with a professional, adaptable document that saves time and ensures accuracy.
You may also like
- IT Brochure
- IT and Software ID Card
- IT Proposal
- IT and Software Plan
- IT Software Business Card
- IT and Software Checklist
- IT and Software Report
- IT Resume
- IT Contract
- IT and Software Form
- It Logo
- IT and Software Presentation
- IT and Software Agreement
- IT and Software Policy
- IT and Software Budget
- IT and Software Quotation
- IT and Software Schedule
- IT and Software Invoice
- IT and Software Newsletter
- IT and Software Receipt