Free IT Security Checklist
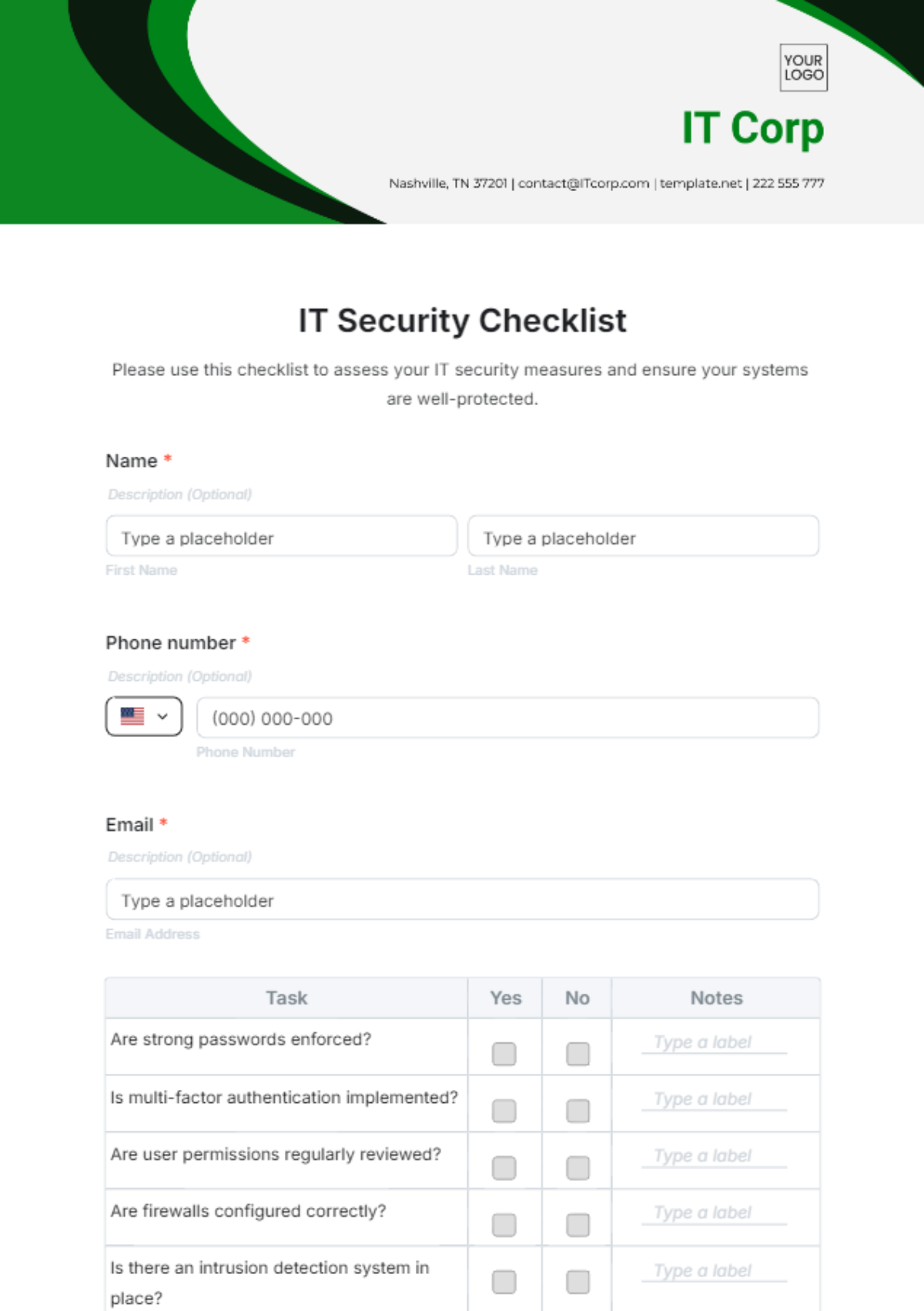
Please use this checklist to assess your IT security measures and ensure your systems are well-protected.
Name
Phone number
Task | Yes | No | Notes |
|---|---|---|---|
Are strong passwords enforced? | | ||
Is multi-factor authentication implemented? | | ||
Are user permissions regularly reviewed? | | ||
Are firewalls configured correctly? | | ||
Is there an intrusion detection system in place? | | ||
Are network devices regularly updated? | | ||
Is sensitive data encrypted? | | ||
Are regular backups performed? | | ||
Is data loss prevention software utilized? | | ||
Are software updates and patches applied promptly? | | ||
Is security software installed on all devices? | | ||
Are vulnerability assessments conducted regularly? | | ||
Are server rooms secured? | | ||
Is access to IT equipment controlled? | | ||
Are surveillance systems in place? | | ||
Is there an incident response plan? | | ||
Are staff trained on incident reporting? | | ||
Are regular incident response drills conducted? | | ||
Are compliance requirements met? | | ||
Is employee security awareness training conducted? | | ||
Are policies regularly reviewed and updated? | |
Are policies regularly reviewed and updated?Are policies regularly reviewed and updated?Are policies regularly reviewed and updated?
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Discover the IT Security Checklist Template on Template.net, designed to streamline your security management. This fully editable and customizable template allows you to tailor each section to your needs. Utilize the AI Editor Tool for effortless updates and precise adjustments, ensuring your IT security practices are always current and comprehensive. Perfect for enhancing organizational security protocols.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist