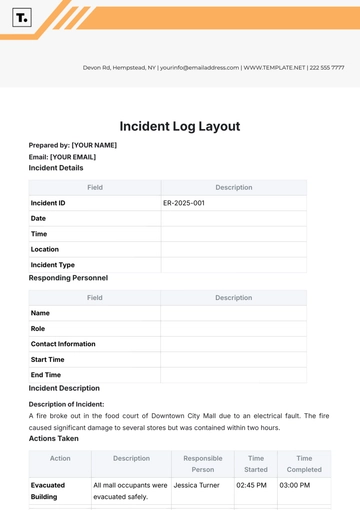
Audit Log Outline
Prepared By
Name: [YOUR NAME]
Email: [YOUR EMAIL]
Company Information
Company Name: [YOUR COMPANY NAME]
Company Number: [YOUR COMPANY NUMBER]
Company Address: [YOUR COMPANY ADDRESS]
Company Website: [YOUR COMPANY WEBSITE]
Company Social Media: [YOUR COMPANY SOCIAL MEDIA]
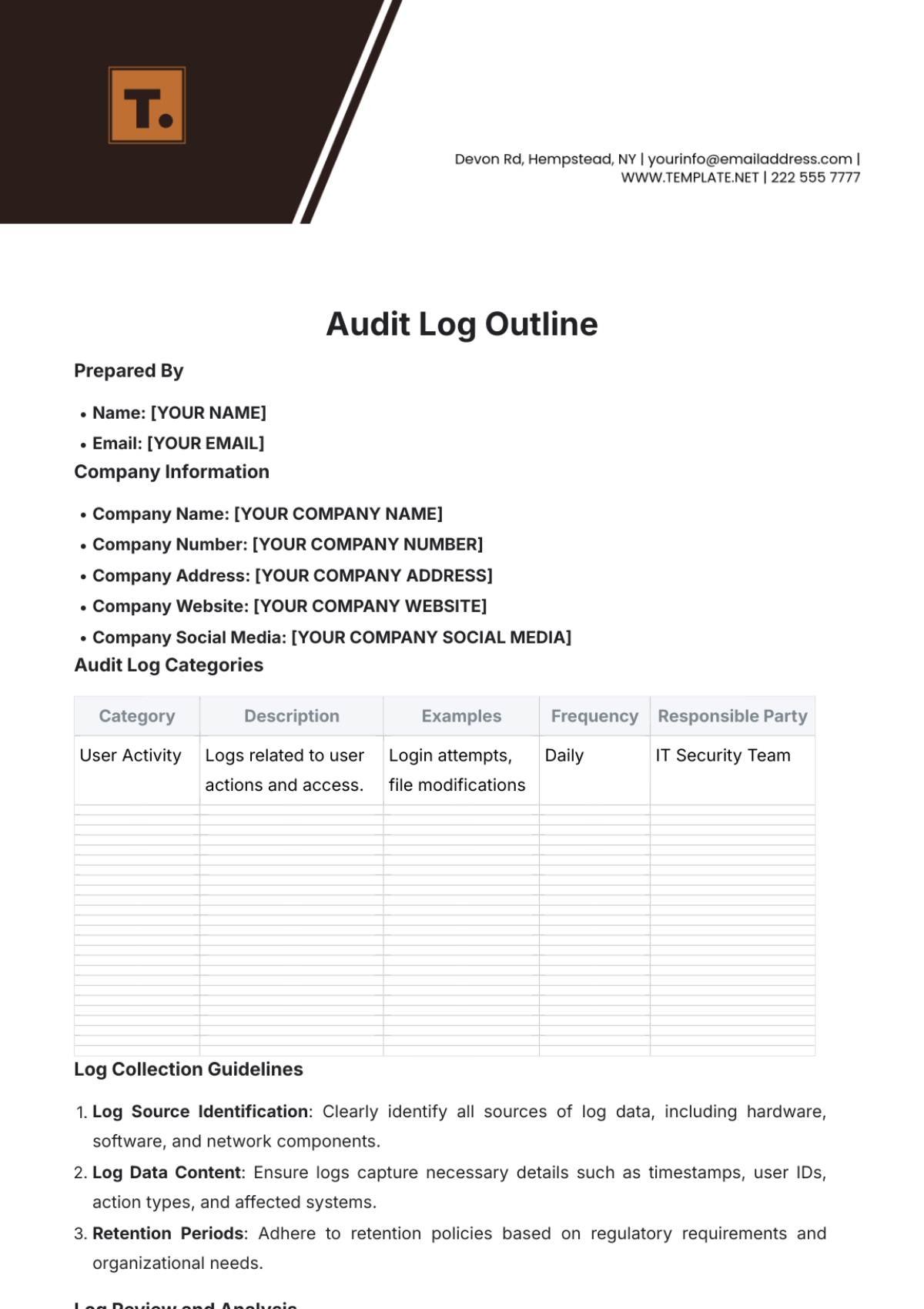
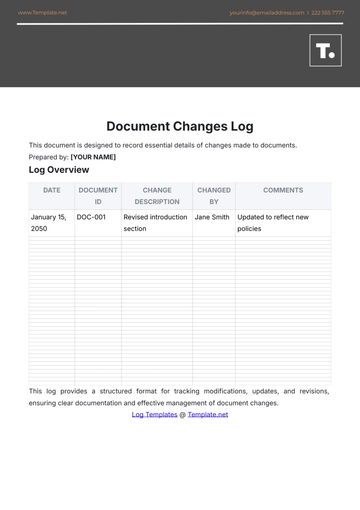
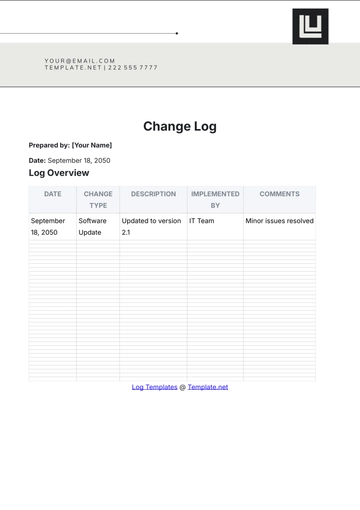
Audit Log Categories
Category | Description | Examples | Frequency | Responsible Party |
|---|
User Activity | Logs related to user actions and access. | Login attempts, file modifications | Daily | IT Security Team |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
Log Collection Guidelines
Log Source Identification: Clearly identify all sources of log data, including hardware, software, and network components.
Log Data Content: Ensure logs capture necessary details such as timestamps, user IDs, action types, and affected systems.
Retention Periods: Adhere to retention policies based on regulatory requirements and organizational needs.
Log Review and Analysis
Review Type | Frequency | Responsibility | Criteria | Notes |
|---|
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
| | | | |
Regular monitoring and analysis of audit logs are essential for maintaining compliance and ensuring the integrity of your systems.
Log Templates @ Template.net