Free Security Service Log
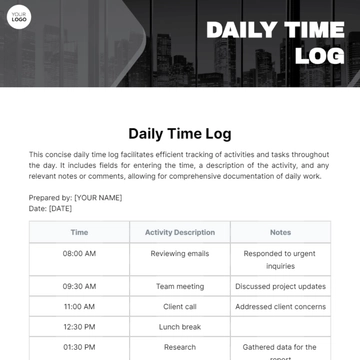
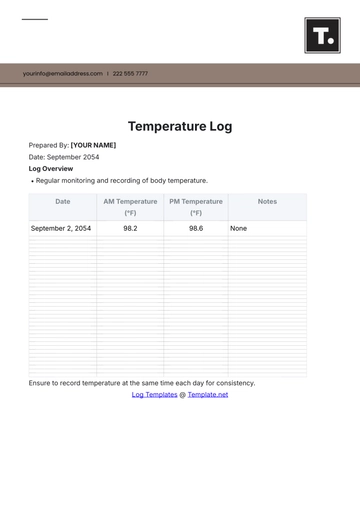
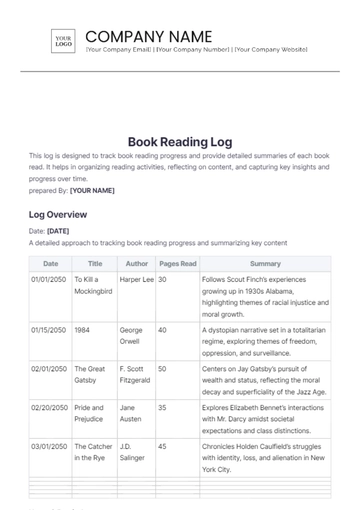
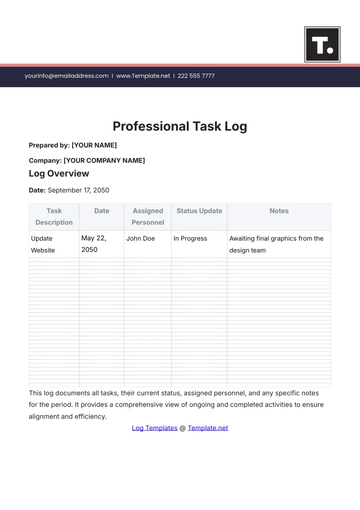
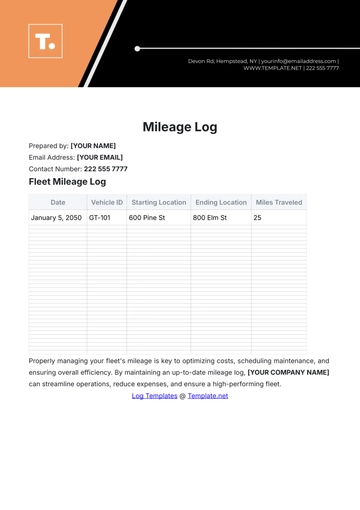
To use this log, provide all necessary details of each security incident, including the date, time, location, description, actions taken, and any follow-up steps. Ensure to include names of those involved and collect signatures for verification. This helps maintain a complete and accurate record for future reference.
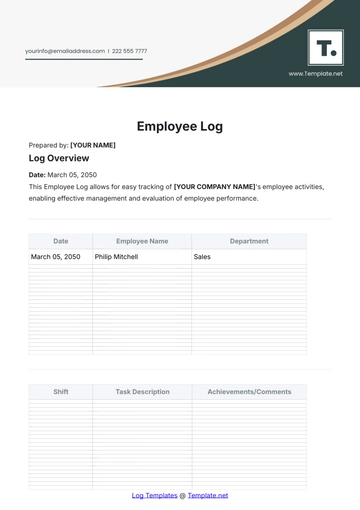
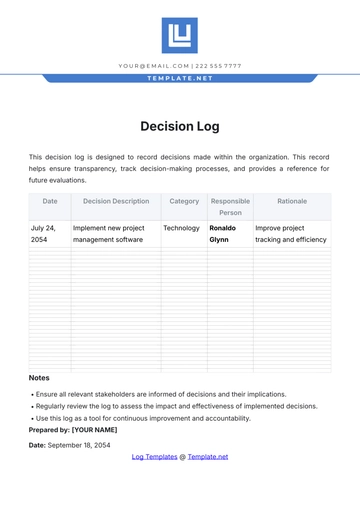
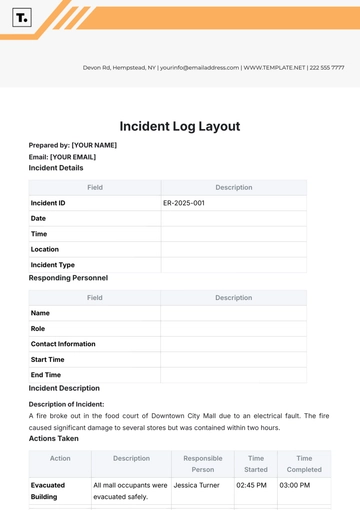
Incident Details Table
Date | Time | Location | Incident Category | Severity Level | Description of Incident |
|---|---|---|---|---|---|
10/24/2050 | 14:30 | Main Entrance | Unauthorized Entry | High | Unauthorized entry attempted by an individual. |
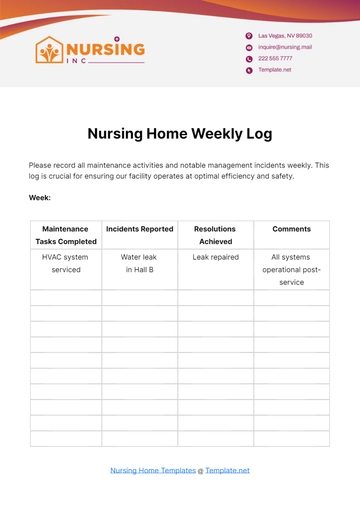
Response Actions Table
Response Action | Action Taken |
|---|---|
Detained individual until law enforcement arrived. | Review access control policies. |
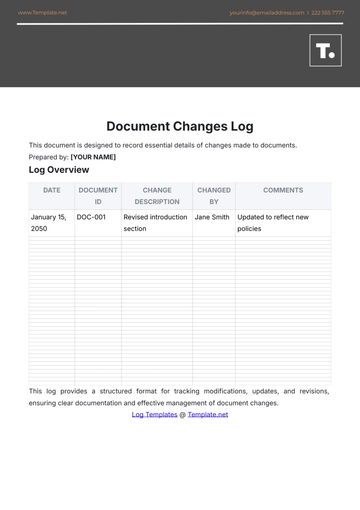
Follow-Up Information Table
Follow-Up Actions | Reported By | Witnesses |
|---|---|---|
Review access control policies. | John Doe, (123) 456-7890 | Jane Smith |
Note:
Ensure all security incidents are logged accurately and followed up promptly to mitigate potential risks and prevent future occurrences.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Document key activities with the Security Service Log Template from Template.net. This editable and customizable template enables you to track various security tasks, from patrols to equipment checks. Personalize it using our Ai Editor Tool to ensure a comprehensive and efficient logging process.