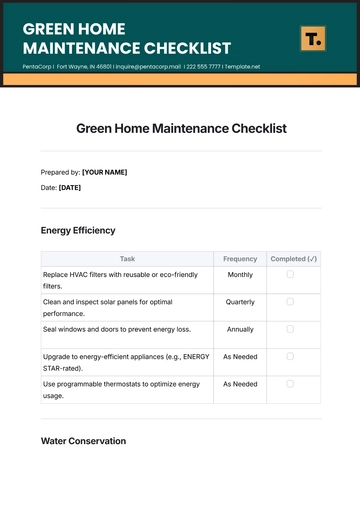
Free Operations IT Security Compliance Checklist

Compliance Checklist
Instruction for Use: This checklist is designed to guide our team through the essential steps to ensure IT security compliance within our operations. Please review each item carefully and mark it as completed once the necessary actions have been taken or confirmed. If any item cannot be completed, note the reason and plan for resolution. Regular audits should be conducted using this checklist to maintain our security posture.
User Access Control
Ensure all employees have unique user IDs for system access.
Implement strong password policies (minimum length, complexity).
Regularly review and update access permissions according to job roles.
Employ multi-factor authentication where possible.
Data Protection
Encrypt sensitive data both in transit and at rest.
Regularly back up critical data with secure storage solutions.
Establish clear data retention and disposal policies.
Network Security
Secure network with firewalls and intrusion detection/prevention systems.
Regularly update anti-virus and anti-malware software on all devices.
Monitor network traffic for unusual activity to detect potential threats.
Physical Security
Secure access to our facilities and data centers with access control systems.
Implement surveillance systems to monitor sensitive areas.
Ensure proper environmental controls are in place to protect IT equipment.
Incident Response and Management
Develop and regularly update an incident response plan.
Conduct periodic drills to ensure readiness for security incidents.
Maintain logs of all security incidents and responses for future review.
Compliance and Audit
Regularly review IT policies and procedures to ensure compliance with relevant laws and regulations.
Conduct internal and external audits of our IT operations and security practices.
Address any compliance gaps identified during audits promptly.
Employee Training and Awareness
Provide ongoing security awareness training for all employees.
Regularly test employees' security awareness (e.g., through phishing simulations).
Update training programs based on current cyber security trends and threats.
Vendor Management
Assess the security measures of third-party vendors and service providers.
Ensure contracts with vendors include provisions for data security and compliance.
Regularly review and monitor vendor compliance with our security requirements.
Software and Systems Security
Ensure secure configuration of all IT systems and applications.
Regularly update and patch operating systems, software, and firmware.
Implement secure development practices for in-house developed applications.
Privacy Compliance
Ensure that our data collection, processing, and storage practices comply with privacy laws and regulations.
Implement mechanisms for data subjects to exercise their privacy rights.
Conduct privacy impact assessments for new projects or data uses.
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Unlock seamless operations security compliance with the Operations IT Security Compliance Checklist Template from Template.net. This fully editable and highly customizable template ensures your IT operations meet industry standards. Tailored to perfection, it's designed for efficiency, editable in our AI Editor tool, providing a straightforward path to compliance.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist