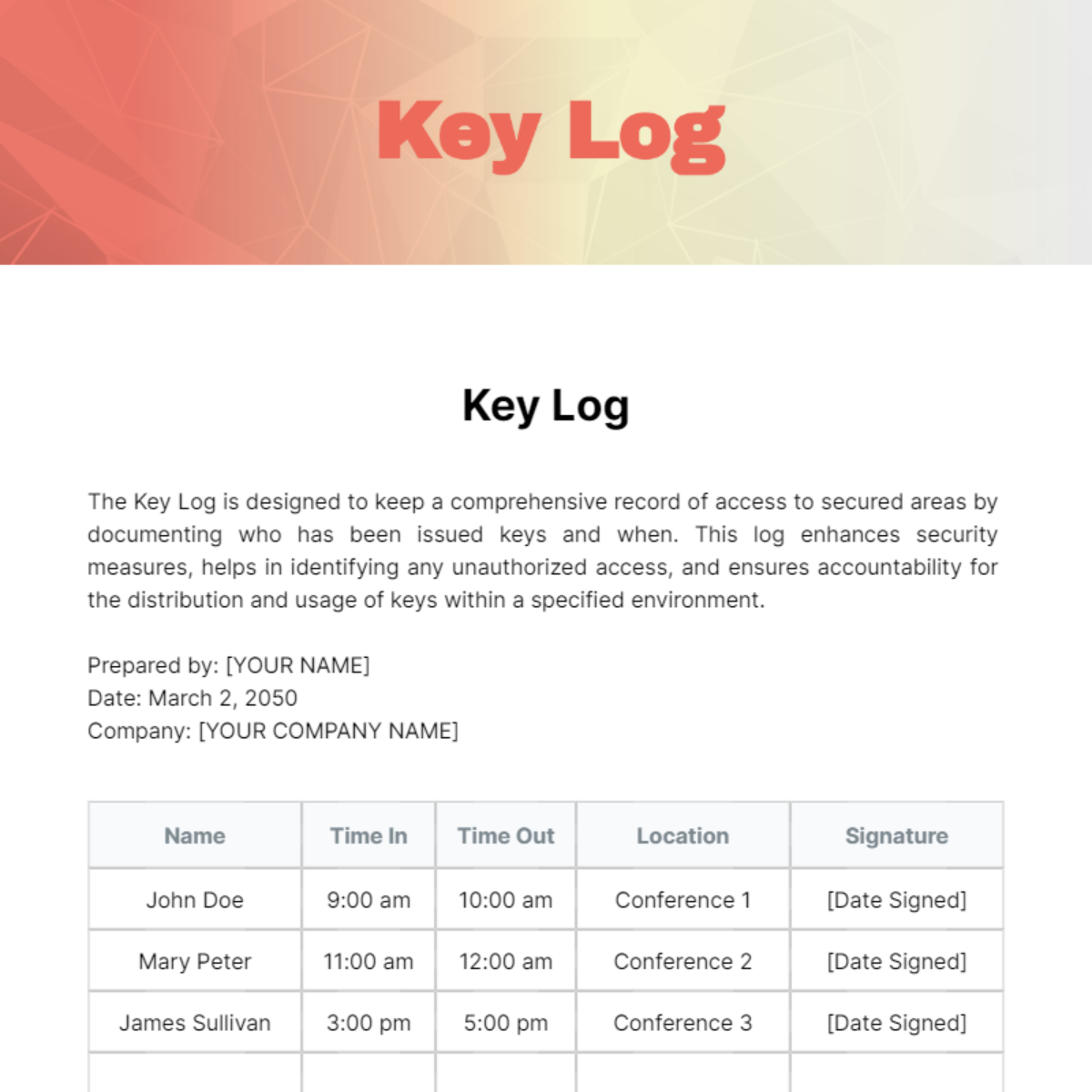
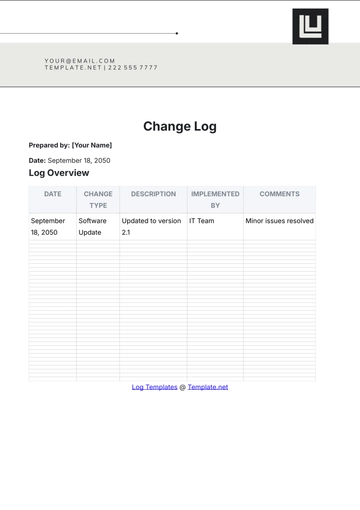
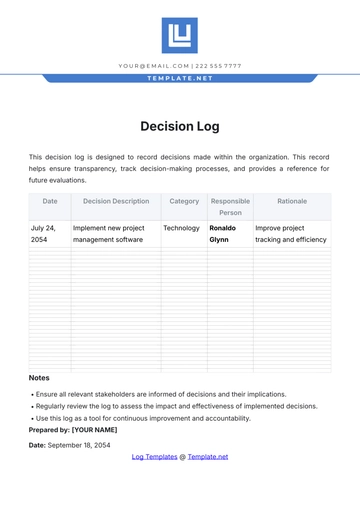
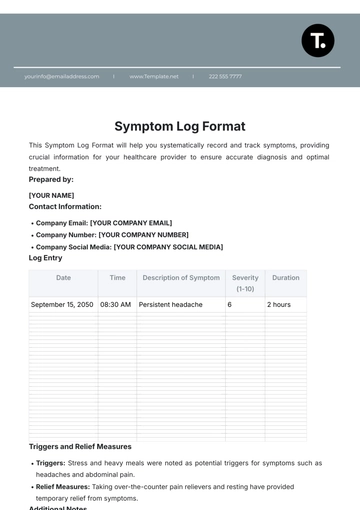
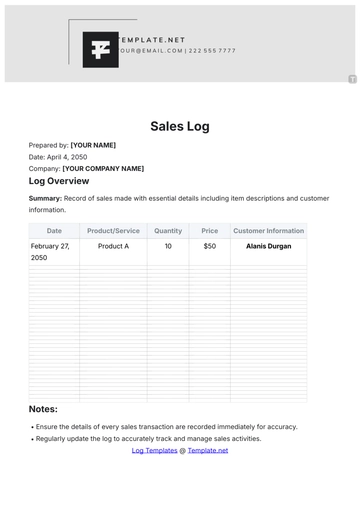
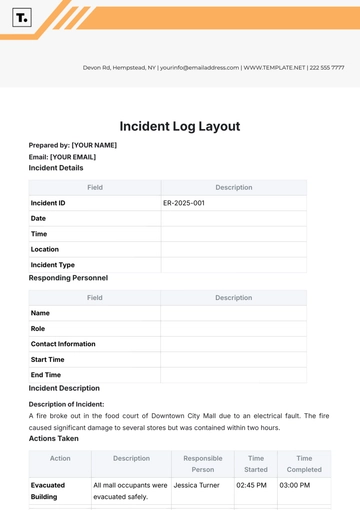
Free Key Log
Enhance and Discover seamless productivity with the Key Log Template from Template.net. This editable and customizable template, designed for utmost convenience, can be effortlessly personalized using our Ai Editor Tool. Seamlessly edit it in our Ai Editor Tool for personalized precision. Elevate your logging experience with this user-friendly, versatile tool.