Free Sample IT Work From Home Setup Checklist
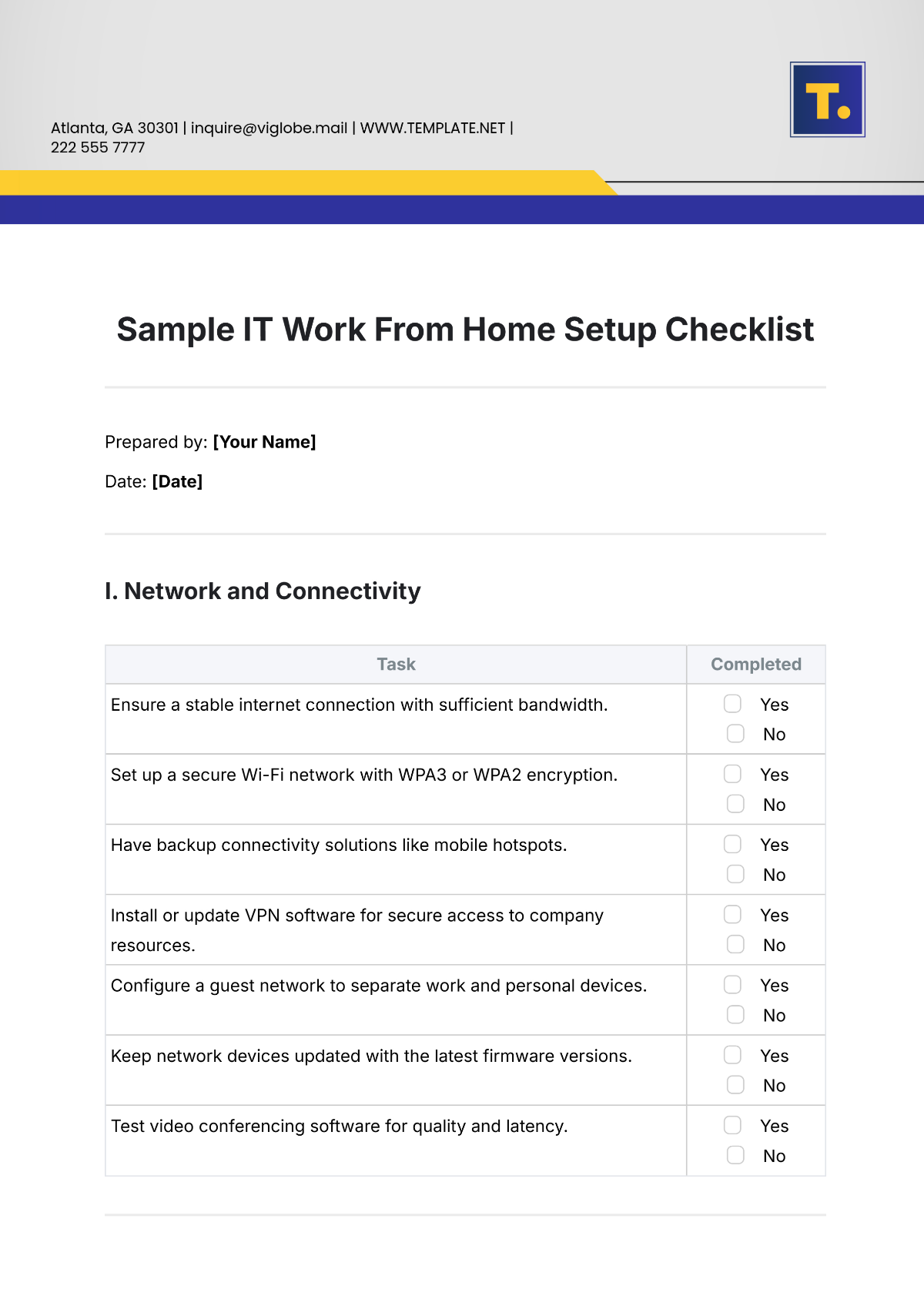
Prepared by: [Your Name]
Date: [Date]
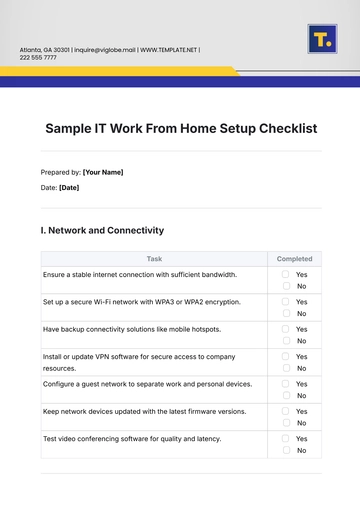
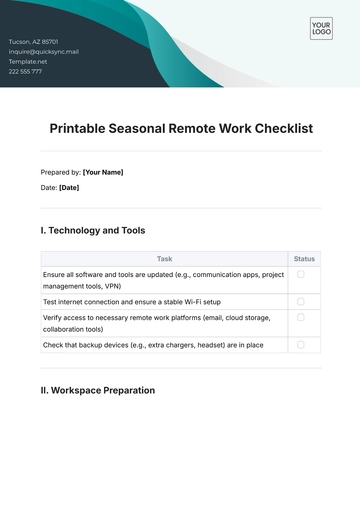
I. Network and Connectivity
Task | Completed |
|---|---|
Ensure a stable internet connection with sufficient bandwidth. |
|
Set up a secure Wi-Fi network with WPA3 or WPA2 encryption. |
|
Have backup connectivity solutions like mobile hotspots. |
|
Install or update VPN software for secure access to company resources. |
|
Configure a guest network to separate work and personal devices. |
|
Keep network devices updated with the latest firmware versions. |
|
Test video conferencing software for quality and latency. |
|
II. Hardware and Peripherals
Task | Completed |
|---|---|
Choose a suitable computer or laptop for work requirements. |
|
Set up an ergonomically correct workstation with a proper chair and desk. |
|
Integrate necessary peripherals like a keyboard, mouse, printer, and monitor. |
|
Ensure an adequate power supply with surge protection. |
|
Check hardware compatibility with work applications and software. |
|
Set up and test communication tools like headsets and webcams. |
|
Organize cables and cords to reduce clutter and improve safety. |
|
III. Software and Applications
Task | Completed |
|---|---|
Install essential productivity tools like office suites and project management software. |
|
Set up secure authentication methods like 2FA for system access. |
|
Regularly update all software to the latest versions for security. |
|
Configure automatic updates to minimize manual maintenance. |
|
Ensure backup software is set up and test restore processes. |
|
Use company-approved cloud solutions for file storage and sharing. |
|
Install antivirus software to protect against malware and threats. |
|
IV. Security Measures
Task | Completed |
|---|---|
Enable and configure firewalls on all devices. |
|
Regularly review and update passwords with strong credentials. |
|
Conduct periodic security audits to identify vulnerabilities. |
|
Train employees to recognize phishing and other cyber threats. |
|
Restrict access to sensitive data to authorized personnel only. |
|
Use encrypted communication channels for confidential information. |
|
Regularly review and update security policies for new threats. |
|
V. Workspace Environment
Task | Completed |
|---|---|
Designate a specific area at home as a temporary office space. |
|
Ensure proper lighting to reduce eye strain and improve focus. |
|
Keep a tidy and organized workstation to enhance productivity. |
|
Optimize room temperature and ventilation for comfort. |
|
Minimize noise distractions with headphones or soundproofing. |
|
Maintain clear separation between work and personal areas. |
|
Ensure easy access to office supplies and equipment. |
|
VI. Communication and Collaboration
Task | Completed |
|---|---|
Set up tools like email, chat, and video conferencing. |
|
Schedule regular check-ins and meetings with team members. |
|
Use shared calendars for meetings and deadlines. |
|
Establish clear communication guidelines for remote interactions. |
|
Utilize team collaboration software for project management. |
|
Ensure IT support is accessible for technical issues. |
|
Foster open communication to address issues promptly. |
|
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Stay organized with the Sample IT Work From Home Setup Checklist Template from Template.net. This fully customizable and editable checklist ensures a seamless remote work experience. Easily personalize it to suit your needs using our Ai Editor Tool. Streamline your setup process and boost productivity with this user-friendly, professional template designed for IT professionals.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist