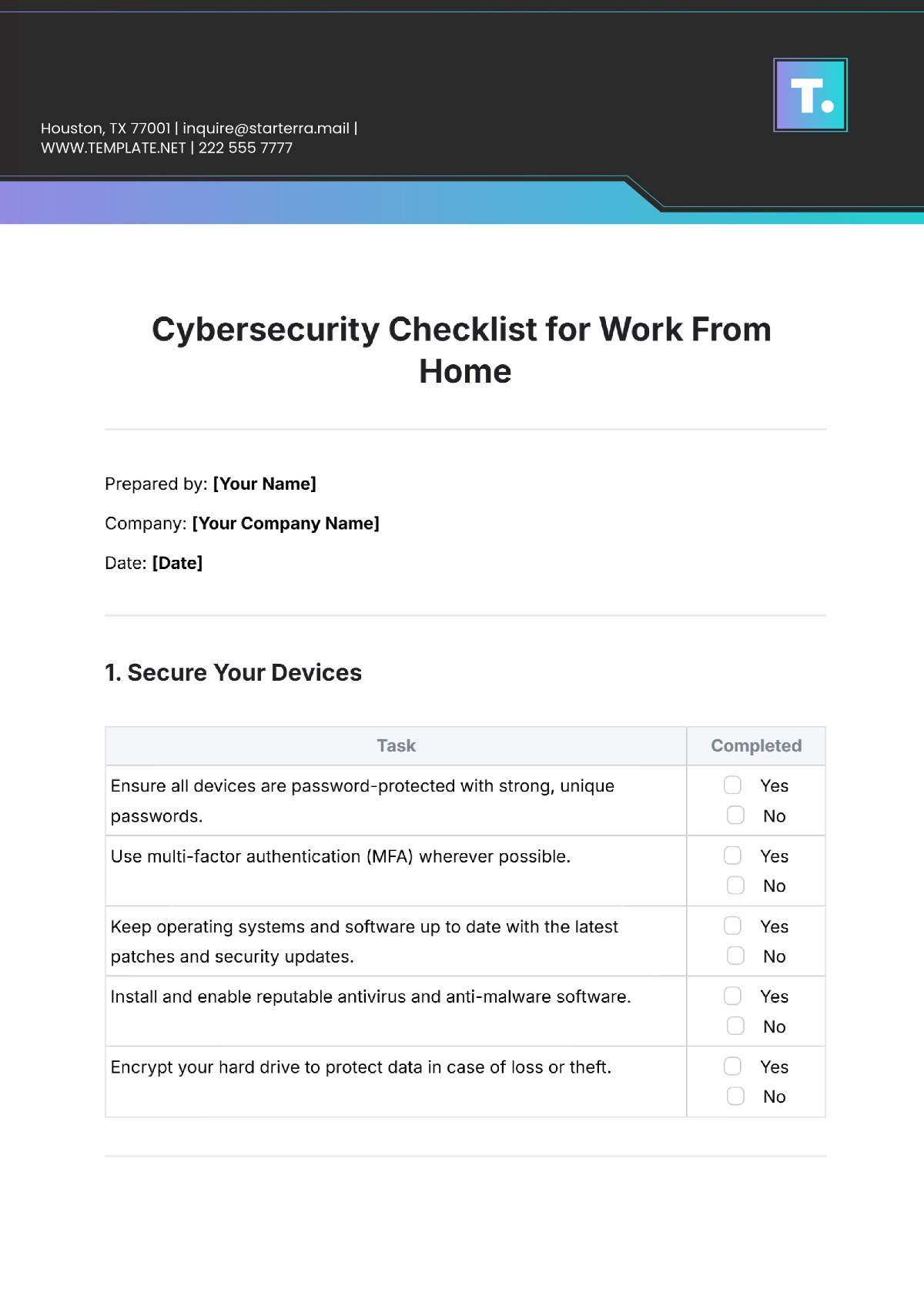
Free Cybersecurity Checklist for Work From Home
Prepared by: [Your Name]
Company: [Your Company Name]
Date: [Date]
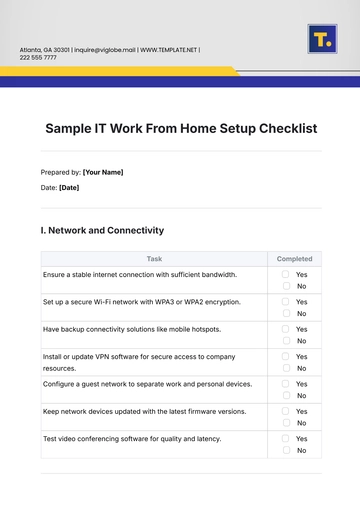
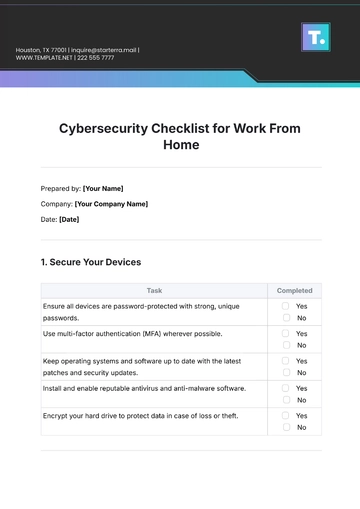
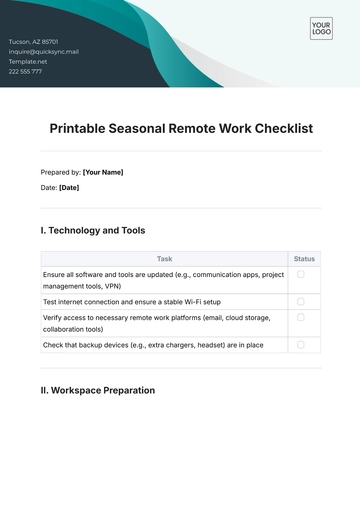
1. Secure Your Devices
Task | Completed |
|---|---|
Ensure all devices are password-protected with strong, unique passwords. |
|
Use multi-factor authentication (MFA) wherever possible. |
|
Keep operating systems and software up to date with the latest patches and security updates. |
|
Install and enable reputable antivirus and anti-malware software. |
|
Encrypt your hard drive to protect data in case of loss or theft. |
|
2. Secure Your Network
Task | Completed |
|---|---|
Use a secure Wi-Fi connection with WPA3/WPA2 encryption. |
|
Change the default router username and password. |
|
Enable a firewall on your router and devices. |
|
Avoid using public Wi-Fi for work activities; use a VPN if public Wi-Fi is necessary. |
|
3. Protect Confidential Data
Task | Completed |
|---|---|
Store sensitive company data in approved, encrypted cloud services. |
|
Avoid saving sensitive files locally on personal devices. |
|
Disable automatic syncing of work data with personal accounts. |
|
Regularly back up important work files to a secure location. |
|
4. Email and Communication Safety
Task | Completed |
|---|---|
Be cautious of phishing emails; check sender addresses and avoid clicking suspicious links. |
|
Report any phishing attempts to the IT team. |
|
Use company-approved communication tools (e.g., Slack, Teams, Zoom). |
|
Avoid sharing sensitive data over unencrypted emails. |
|
5. Physical Security
Task | Completed |
|---|---|
Lock your devices when not in use, even at home. |
|
Keep your workspace free from unauthorized access (e.g., roommates, family members). |
|
Store physical work documents in a locked cabinet or drawer. |
|
Shred any printed documents containing confidential information. |
|
6. Password and Authentication Management
Task | Completed |
|---|---|
Use a password manager to store and generate strong passwords. |
|
Avoid reusing passwords across accounts. |
|
Change passwords periodically and immediately after suspected compromise. |
|
7. Video Conferencing Security
Task | Completed |
|---|---|
Use meeting passwords and waiting rooms to secure video calls. |
|
Avoid sharing meeting links publicly. |
|
Turn off recording unless necessary and store recordings securely. |
|
Be mindful of what’s visible in your background during video calls. |
|
8. Use Company-Issued Devices
Task | Completed |
|---|---|
Work only on company-provided devices if available. |
|
Avoid using personal devices for work activities unless approved by IT. |
|
Do not install unauthorized software on work devices. |
|
9. Stay Vigilant for Cyber Threats
Task | Completed |
|---|---|
Monitor unusual activity, such as unexpected pop-ups or system slowdowns. |
|
Report any suspicious activities or potential breaches to the IT team immediately. |
|
Stay updated with company policies regarding cybersecurity. |
|
10. Maintain a Safe Work Environment
Task | Completed |
|---|---|
Be aware of shoulder surfing (others viewing your screen). |
|
Avoid printing sensitive documents unless necessary. |
|
Regularly review and follow company cybersecurity policies. |
|
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Ensure secure remote work with the Cybersecurity Checklist for Work From Home Template from Template.net. This customizable and editable checklist simplifies implementing security measures. Editable in our Ai Editor Tool, it’s perfect for creating tailored cybersecurity plans. Protect sensitive data and streamline processes with ease—boost productivity while prioritizing safety.
You may also like
- Cleaning Checklist
- Daily Checklist
- Travel Checklist
- Self Care Checklist
- Risk Assessment Checklist
- Onboarding Checklist
- Quality Checklist
- Compliance Checklist
- Audit Checklist
- Registry Checklist
- HR Checklist
- Restaurant Checklist
- Checklist Layout
- Creative Checklist
- Sales Checklist
- Construction Checklist
- Task Checklist
- Professional Checklist
- Hotel Checklist
- Employee Checklist
- Moving Checklist
- Marketing Checklist
- Accounting Checklist
- Camping Checklist
- Packing Checklist
- Real Estate Checklist
- Cleaning Checklist Service
- New Employee Checklist
- Food Checklist
- Home Inspection Checklist
- Advertising Checklist
- Event Checklist
- SEO Checklist
- Assessment Checklist
- Inspection Checklist
- Baby Registry Checklist
- Induction Checklist
- Employee Training Checklist
- Medical Checklist
- Safety Checklist
- Site Checklist
- Job Checklist
- Service Checklist
- Nanny Checklist
- Building Checklist
- Work Checklist
- Office Checklist
- Training Checklist
- Website Checklist
- IT and Software Checklist
- Performance Checklist
- Project Checklist
- Startup Checklist
- Education Checklist
- Home Checklist
- School Checklist
- Maintenance Checklist
- Planning Checklist
- Manager Checklist
- Wedding Checklist
- Vehicle Checklist
- Travel Agency Checklist
- Vehicle Inspection Checklist
- Interior Design Checklist
- Backpacking Checklist
- Business Checklist
- Legal Checklist
- Nursing Home Checklist
- Weekly Checklist
- Recruitment Checklist
- Salon Checklist
- Baby Checklist
- Equipment Checklist
- Trade Show Checklist
- Party Checklist
- Hospital Bag Checklist
- Evaluation Checklist
- Agency Checklist
- First Apartment Checklist
- Hiring Checklist
- Opening Checklist
- Small Business Checklist
- Rental Checklist
- College Dorm Checklist
- New Puppy Checklist
- University Checklist
- Building Maintenance Checklist
- Work From Home Checklist
- Student Checklist
- Application Checklist