Free Cybersecurity Incident Emergency Response Plan

I. Executive Summary
[Your Company Name]'s Cybersecurity Incident Emergency Response Plan is a cornerstone of our organization's defense against the ever-evolving landscape of cyber threats. This comprehensive plan is constructed to manage and mitigate the impact of cybersecurity incidents through a multifaceted approach. It encompasses stringent proactive measures, including regular system audits, advanced threat detection algorithms, and employee cybersecurity awareness programs. These initiatives are aimed at preventing incidents before they occur, minimizing vulnerabilities, and ensuring that all personnel are equipped with the knowledge to identify and report potential threats promptly.
Our plan further delineates rapid response protocols tailored to a spectrum of cyber threats, from data breaches and ransomware attacks to network intrusions and phishing attempts. In the event of an incident, our specialized Cybersecurity Incident Response Team (CIRT) is mobilized to swiftly contain and assess the threat, implement effective countermeasures, and mitigate any operational or data-related impacts. Following an incident, the plan outlines a structured recovery process, focusing on restoring affected systems and data integrity. Alongside, it ensures business continuity through well-prepared backup systems and contingency protocols. This dual focus on immediate response and long-term recovery underscores our commitment to resilience and the safeguarding of our vital digital assets against cyber threats.
II. Identification of Critical Assets and Systems
The identification and protection of critical IT assets are paramount for [Your Company Name]. Our focus extends to a broad array of digital assets that are integral to our operations and client trust. This includes sensitive customer data, which encompasses personal and financial information, necessitating stringent security measures. Proprietary software, which forms the backbone of our service offerings, is another critical asset, requiring constant vigilance against unauthorized access and intellectual property theft. Financial records, essential for our operational integrity and regulatory compliance, are safeguarded through encrypted storage and controlled access mechanisms.
To ensure the security and integrity of these assets, [Your Company Name] engages in regular and comprehensive audits. These audits are meticulously designed to identify any vulnerabilities within our systems, ranging from outdated software to potential gaps in network security. This process is not static but an ongoing endeavor, adapting to new threats and incorporating the latest cybersecurity best practices. We place a strong emphasis on not just identifying and protecting these assets but also on establishing a proactive culture of security awareness across all levels of the organization. This approach includes regular updates and upgrades to our security infrastructure, ensuring that our critical assets remain resilient against the continuously evolving landscape of cyber threats.
III. Risk Assessment and Threat Analysis
[Your Company Name]’s approach to risk assessment and threat analysis in cybersecurity is thorough and dynamic, reflecting the evolving nature of cyber threats. Our team of cybersecurity experts continuously evaluates the landscape for potential risks such as malware attacks, which can disrupt critical systems and compromise sensitive data. Data breaches are scrutinized for their potential to expose confidential information, while unauthorized access is assessed for risks to our network integrity and operational security. This ongoing risk assessment process involves analyzing not just the likelihood of these threats but also their potential severity and impact on our business operations. We leverage advanced analytical tools and threat intelligence sources to stay ahead of potential risks, ensuring our defenses are both robust and proactive.
Furthermore, our threat analysis extends to examining the potential impacts of these cybersecurity risks on different aspects of our business. This includes assessing the consequences on client trust and relationships, operational downtime, legal and regulatory compliance, and financial liabilities. By understanding the multi-dimensional impacts of cyber threats, we can prioritize our security measures effectively, focusing on the most critical areas of vulnerability. This comprehensive view allows us to develop and refine targeted strategies to strengthen our cyber defenses, ensuring that [Your Company Name] is not only prepared to respond to immediate threats but also equipped to handle long-term cybersecurity challenges.
IV. Cybersecurity Incident Response Team (CIRT) Structure and Contact Information
CIRT Leader | [Name] | Oversees incident response operations | [Office number, mobile number, email address] |
IT Security Officer | [Name] | Responsible for technical analysis and containment measures | [Office number, mobile number, email address] |
Legal Advisor | [Name] | Ensure compliance with legal and regulatory requirements during and after incidents | [Office number, mobile number, email address] |
V. Incident Detection and Reporting Procedures
[Your Company Name] uses a suite of sophisticated monitoring tools and procedures to enhance our capabilities in detecting potential cybersecurity incidents swiftly and accurately.
A. Intrusion Detection Systems (IDS):
Our network is safeguarded with state-of-the-art IDS that continuously monitor network traffic for signs of unusual or unauthorized activities. These systems are equipped with heuristic and anomaly-based detection capabilities, allowing them to identify not just known threats but also new, emerging patterns that could signify a breach or an attack.
B. Security Information and Event Management (SIEM) System:
We employ a comprehensive SIEM system that aggregates and analyzes data from various sources within our IT infrastructure. This system correlates events from servers, databases, and applications, providing real-time analysis and alerts for potential security incidents. The SIEM’s advanced analytics play a crucial role in early detection, enabling us to respond to threats before they escalate.
C. Endpoint Detection and Response (EDR) Solutions:
To protect against threats at the device level, we implement EDR solutions across all endpoints in our network. These tools continuously monitor and collect data from endpoints, employing advanced analytics to identify suspicious behavior patterns. EDR solutions provide an additional layer of defense, ensuring rapid detection and response capabilities for threats directly targeting employee devices.
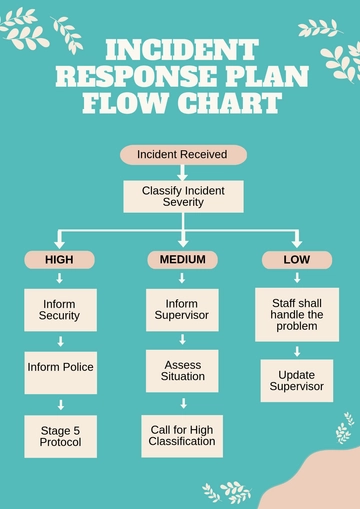
VI. Incident Response Procedures
Upon the detection of a cybersecurity incident, [Your Company Name] activates its Cybersecurity Incident Response Team (CIRT), a specialized unit trained to manage and neutralize cyber threats swiftly and effectively.
A. Containment of the Threat:
The initial focus of the CIRT is to contain the incident to prevent further spread or escalation. This may involve isolating affected systems or networks, temporarily restricting access to certain areas of the IT infrastructure, and implementing additional security measures to halt the progression of the incident. Quick containment is crucial to limit the impact on our operations and protect sensitive data from further compromise.
B. Eradication and Root Cause Analysis:
Once containment is achieved, the team works diligently to identify and eradicate the source of the threat. This phase involves in-depth analysis to understand the nature of the incident, whether it’s a malware infection, a breach by an external attacker, or an internal security lapse. Sophisticated forensic tools are employed to trace the origins of the incident, understand how security defenses were bypassed, and remove any malicious elements from our systems.
C. Recovery and Restoration:
Following the eradication of the threat, the CIRT oversees the recovery process to restore affected systems and services to full functionality. This process is carried out methodically to ensure that no traces of the threat remain and that systems are restored to their secure state. Simultaneously, efforts are made to strengthen system defenses to prevent recurrence of similar incidents.
D. Customized Response Actions:
Our incident response procedures are not one-size-fits-all but are customized based on the type and severity of the incident. For instance, the response to a data breach involves different steps compared to a ransomware attack. This tailored approach ensures that the response is appropriate and effective for the specific nature of each incident.
VII. Communication Plan
During a cybersecurity incident, we maintain clear communication lines internally and externally. This includes timely updates to stakeholders and, if necessary, public statements to manage any external impacts.
VIII. Data Breach Response and Notification Procedures
In the event of a data breach, we follow strict procedures for containment, assessment, and notification to affected parties in compliance with relevant data protection laws. This includes immediate steps to prevent further data loss and notification to regulatory bodies and affected individuals.
IX. Recovery and Business Continuity Plans
Our recovery plan focuses on quickly restoring critical IT functions to minimize operational disruptions. This is complemented by a business continuity plan to maintain essential business operations while IT systems are being restored.
X. Training and Awareness Programs
Regular training sessions and awareness programs are conducted for all employees, focusing on cybersecurity best practices, threat recognition, and response protocols.
XI. Plan Review and Maintenance
The Cybersecurity Incident Emergency Response Plan is reviewed and updated bi-annually or following significant incidents to incorporate new threats, technological advancements, and insights from recent incidents.
Prepared by:
[Your Name],
[Your Job Title]
[Your Company Name]
- 100% Customizable, free editor
- Access 1 Million+ Templates, photo’s & graphics
- Download or share as a template
- Click and replace photos, graphics, text, backgrounds
- Resize, crop, AI write & more
- Access advanced editor
Protect your digital assets swiftly with Template.net's Cybersecurity Incident Emergency Response Plan Template. Crafted for ease, this editable and customizable template integrates seamlessly with our Ai Editor Tool, enabling you to tailor your response plan effortlessly. Stay ahead of threats and mitigate risks effectively with Template.net's cutting-edge solutions.
You may also like
- Finance Plan
- Construction Plan
- Sales Plan
- Development Plan
- Career Plan
- Budget Plan
- HR Plan
- Education Plan
- Transition Plan
- Work Plan
- Training Plan
- Communication Plan
- Operation Plan
- Health And Safety Plan
- Strategy Plan
- Professional Development Plan
- Advertising Plan
- Risk Management Plan
- Restaurant Plan
- School Plan
- Nursing Home Patient Care Plan
- Nursing Care Plan
- Plan Event
- Startup Plan
- Social Media Plan
- Staffing Plan
- Annual Plan
- Content Plan
- Payment Plan
- Implementation Plan
- Hotel Plan
- Workout Plan
- Accounting Plan
- Campaign Plan
- Essay Plan
- 30 60 90 Day Plan
- Research Plan
- Recruitment Plan
- 90 Day Plan
- Quarterly Plan
- Emergency Plan
- 5 Year Plan
- Gym Plan
- Personal Plan
- IT and Software Plan
- Treatment Plan
- Real Estate Plan
- Law Firm Plan
- Healthcare Plan
- Improvement Plan
- Media Plan
- 5 Year Business Plan
- Learning Plan
- Marketing Campaign Plan
- Travel Agency Plan
- Cleaning Services Plan
- Interior Design Plan
- Performance Plan
- PR Plan
- Birth Plan
- Life Plan
- SEO Plan
- Disaster Recovery Plan
- Continuity Plan
- Launch Plan
- Legal Plan
- Behavior Plan
- Performance Improvement Plan
- Salon Plan
- Security Plan
- Security Management Plan
- Employee Development Plan
- Quality Plan
- Service Improvement Plan
- Growth Plan
- Incident Response Plan
- Basketball Plan
- Emergency Action Plan
- Product Launch Plan
- Spa Plan
- Employee Training Plan
- Data Analysis Plan
- Employee Action Plan
- Territory Plan
- Audit Plan
- Classroom Plan
- Activity Plan
- Parenting Plan
- Care Plan
- Project Execution Plan
- Exercise Plan
- Internship Plan
- Software Development Plan
- Continuous Improvement Plan
- Leave Plan
- 90 Day Sales Plan
- Advertising Agency Plan
- Employee Transition Plan
- Smart Action Plan
- Workplace Safety Plan
- Behavior Change Plan
- Contingency Plan
- Continuity of Operations Plan
- Health Plan
- Quality Control Plan
- Self Plan
- Sports Development Plan
- Change Management Plan
- Ecommerce Plan
- Personal Financial Plan
- Process Improvement Plan
- 30-60-90 Day Sales Plan
- Crisis Management Plan
- Engagement Plan
- Execution Plan
- Pandemic Plan
- Quality Assurance Plan
- Service Continuity Plan
- Agile Project Plan
- Fundraising Plan
- Job Transition Plan
- Asset Maintenance Plan
- Maintenance Plan
- Software Test Plan
- Staff Training and Development Plan
- 3 Year Plan
- Brand Activation Plan
- Release Plan
- Resource Plan
- Risk Mitigation Plan
- Teacher Plan
- 30 60 90 Day Plan for New Manager
- Food Safety Plan
- Food Truck Plan
- Hiring Plan
- Quality Management Plan
- Wellness Plan
- Behavior Intervention Plan
- Bonus Plan
- Investment Plan
- Maternity Leave Plan
- Pandemic Response Plan
- Succession Planning
- Coaching Plan
- Configuration Management Plan
- Remote Work Plan
- Self Care Plan
- Teaching Plan
- 100-Day Plan
- HACCP Plan
- Student Plan
- Sustainability Plan
- 30 60 90 Day Plan for Interview
- Access Plan
- Site Specific Safety Plan