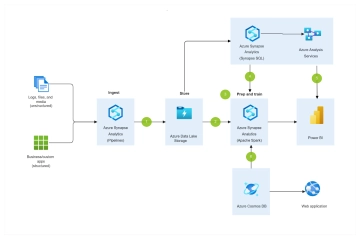
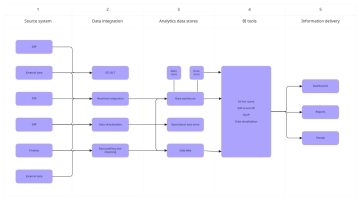
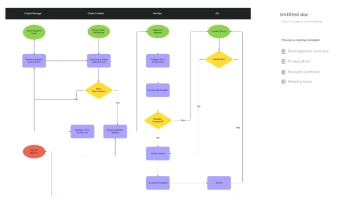
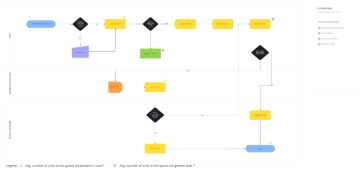
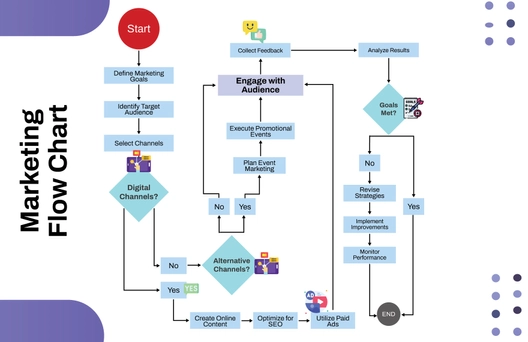
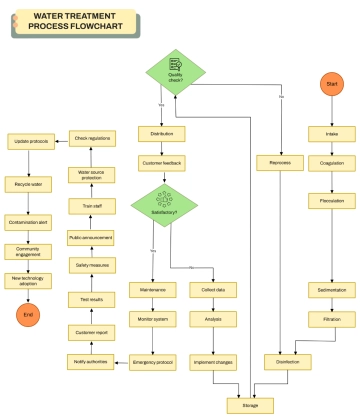
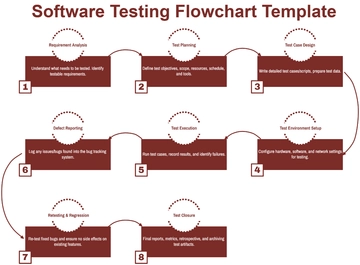
Free Data Encryption Flow Chart
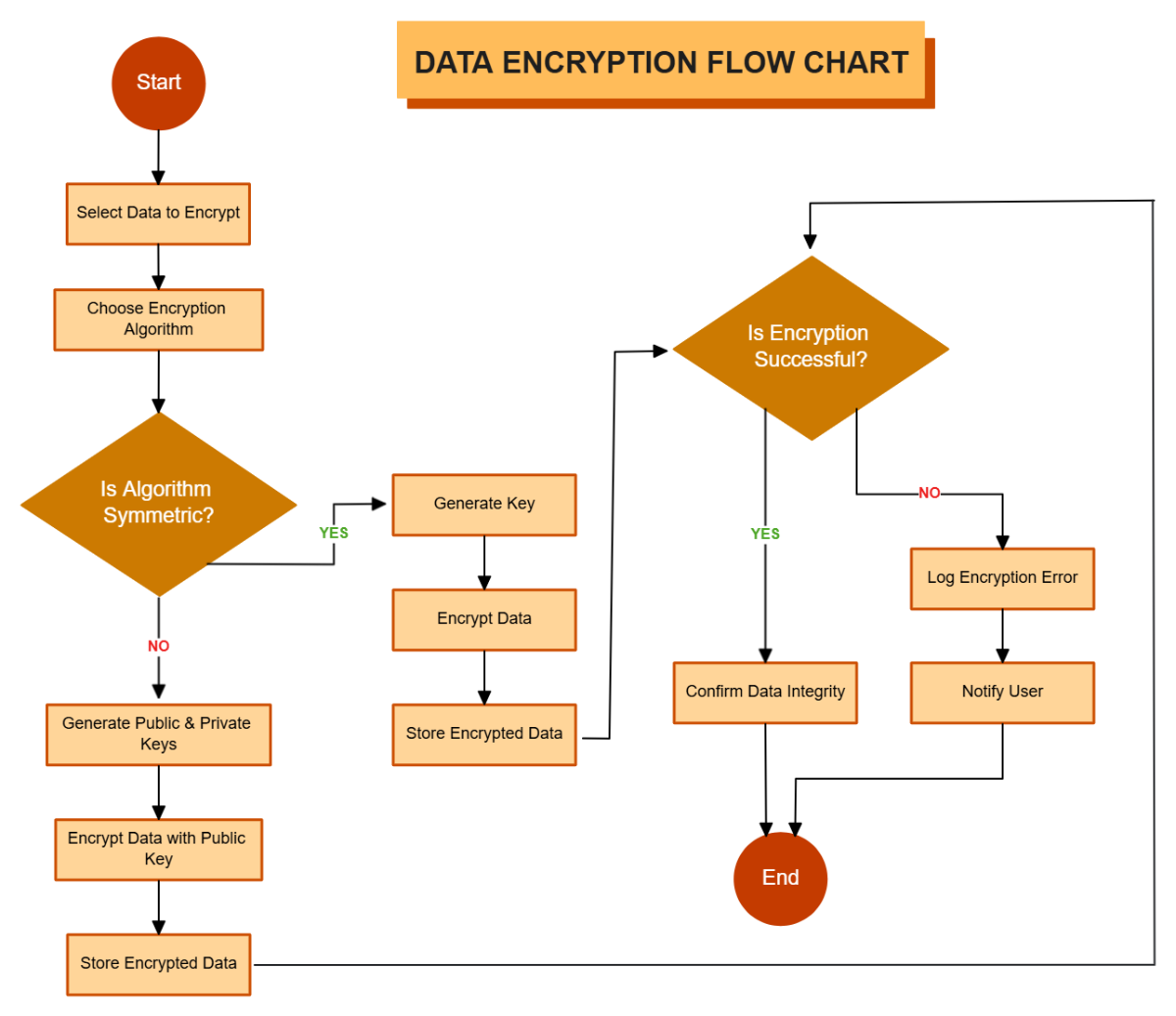
The Data Encryption Flow Chart provides a detailed overview of the process for securing data through encryption. It begins by selecting the data to be encrypted, followed by choosing an appropriate encryption algorithm. A decision point determines whether the algorithm is symmetric or asymmetric. For symmetric encryption, a single key is generated and used for both encryption and decryption. For asymmetric encryption, a pair of public and private keys is generated, and data is encrypted using the public key. Once the encryption process is complete, the encrypted data is securely stored. The next step verifies whether the encryption was successful; if it fails, the system logs an encryption error and notifies the user. If successful, data integrity is confirmed to ensure the information remains accurate and unaltered. The process concludes with a secure, verified encryption outcome, ensuring the confidentiality, integrity, and protection of sensitive digital data against unauthorized access.