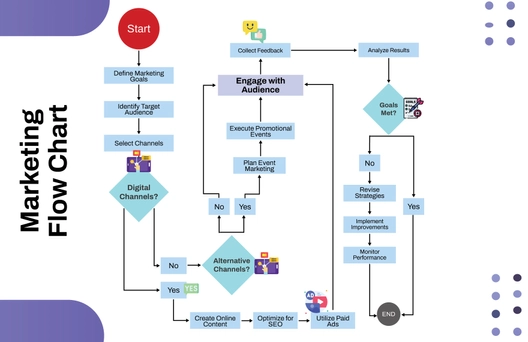
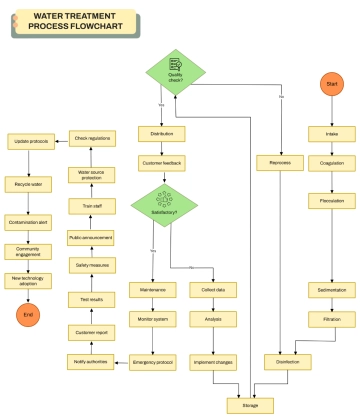
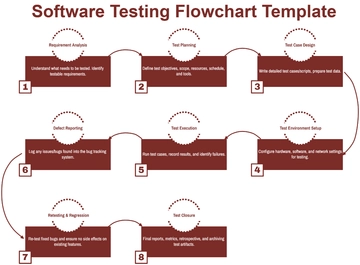
Free 0.Cybersecurity Flow Chart
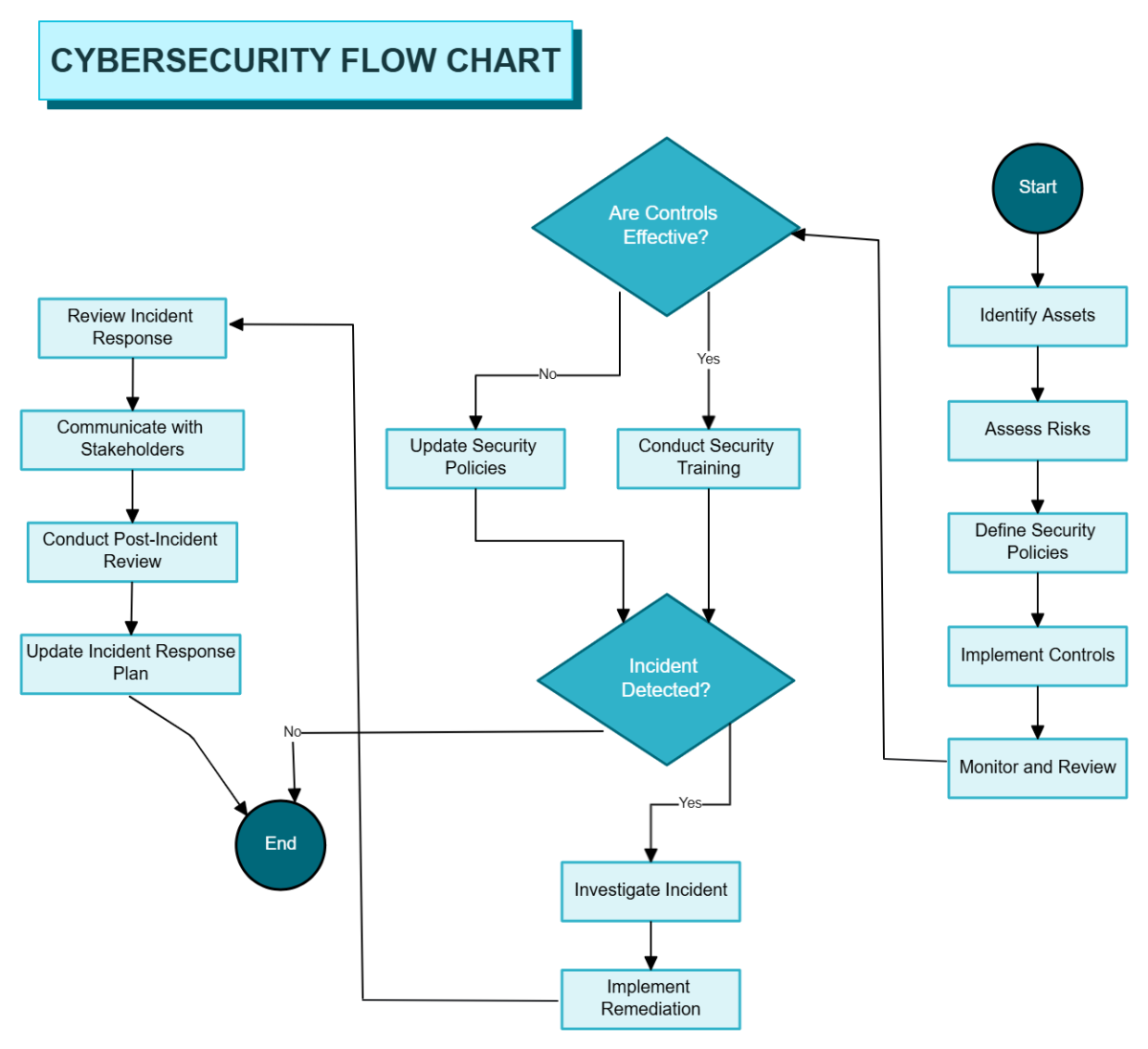
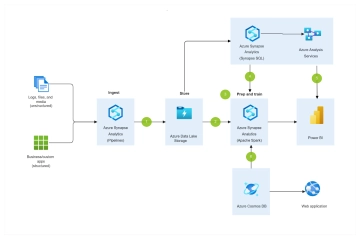
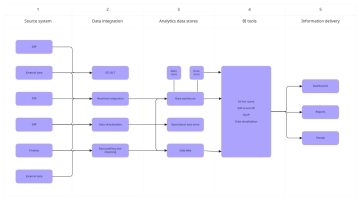
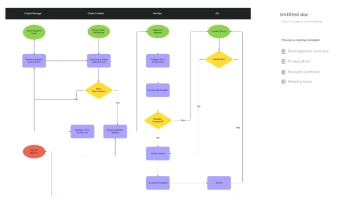
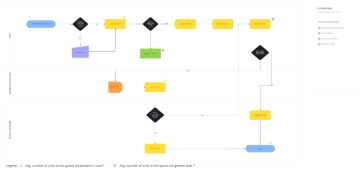
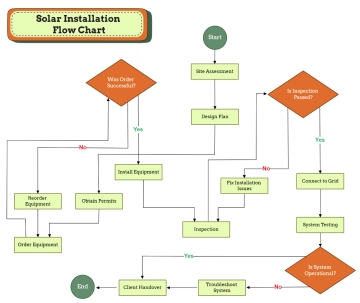
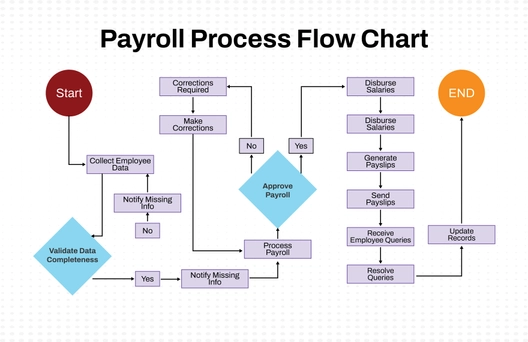
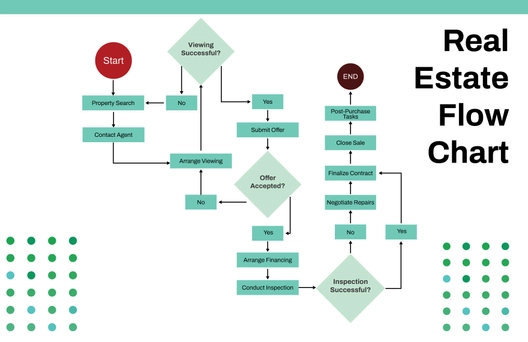
The Cybersecurity Flow Chart illustrates a systematic approach to maintaining and strengthening an organization’s security posture. It begins with identifying assets and assessing risks to determine potential vulnerabilities. Once risks are understood, security policies are defined and controls are implemented to safeguard systems and data. The process then involves continuous monitoring and review to ensure controls remain effective. If controls are found ineffective, security policies are updated to address weaknesses. When controls are effective, regular security training is conducted to reinforce best practices. If an incident is detected, it is investigated thoroughly, and remediation measures are implemented to mitigate the impact. Following an incident, the organization reviews its response, communicates findings with stakeholders, conducts a post-incident review, and updates the incident response plan accordingly. This flowchart emphasizes proactive protection, continuous improvement, and effective incident handling to ensure organizational resilience against cybersecurity threats.